EMC DES-9131 - Specialist - Infrastructure Security Exam
A new employee is starting work at your company. When should they be informed of the company’s security policy?
The Backup Recovery Plan is dependent on what effort?
Refer to the exhibit.
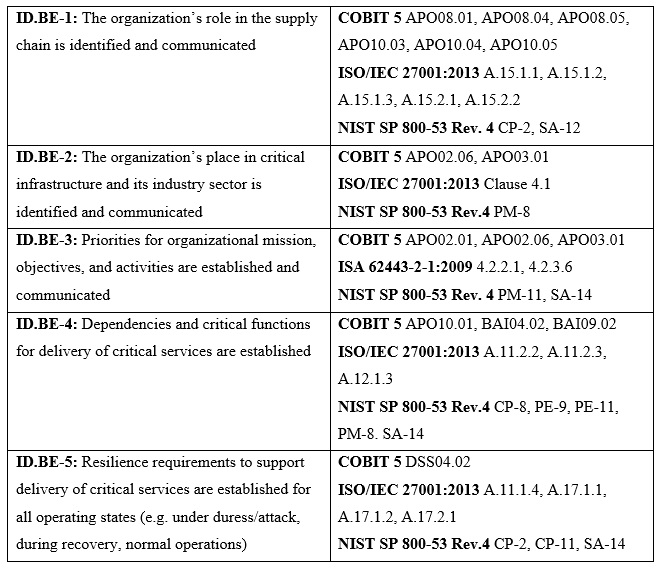
What type of item appears in the second column of the table?
You need to review your current security baseline policy for your company and determine which security
controls need to be applied to the baseline and what changes have occurred since the last update.
Which category addresses this need?
What process is used to identify an organization’s physical, digital, and human resource, as required in their Business Impact Analysis?
What defines who is accountable for contacting operational teams, managers, and others affected by a
localized, safety critical event?
An Internet-connected file server compromised by a threat that leaked all datA. The data was destroyed to cover all tracks. The file server has high availability capabilities to handle critical workloads. The operations team took only 15 minutes to restore workload routing to a different node.
What part(s) of the CIA Triad was affected?
During what activity does an organization identify and prioritize technical, organizational, procedural,
administrative, and physical security weaknesses?



