Trend Micro Deep-Security-Professional - Trend Micro Certified Professional for Deep Security Exam
Total 73 questions
Based on the policy configuration displayed in the exhibit, which of the following statements is true?
Which Deep Security Protection Modules can be used to provide runtime protection for the Kubernetes and Docker platforms? Select all that apply.
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you de-termine which Intrusion Prevention rules are no longer needed on this Server?
Your VMware environment is configured without using NSX. How can Deep Security provide protection to the virtual images hosted on your ESXi servers?
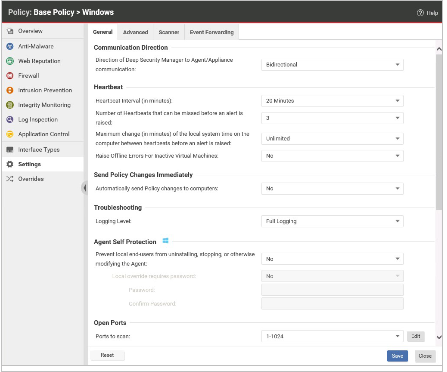
Which of the following statements is correct regarding the policy settings displayed in the exihibit?
What is IntelliScan?
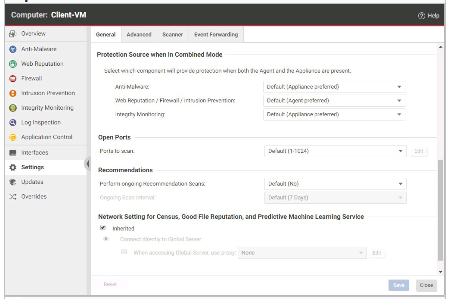
The "Protection Source when in Combined Mode" settings are configured for a virtual machine as in the exhibit. You would like to enable Application Control on this virtual machine, but there is no corresponding setting displayed. Why?
An administrator enables Multi-Tenancy in Deep Security and creates multiple tenants. After a period of time, the administrator would like to review the usage and resource consumption by a specific tenant. How can the administrator retrieve this information?
Which of the following Protection Modules does not benefit from Recommendation Scans?
Which of the following is not an operation that is performed when network traffic is intercepted by the network driver on the Deep Security Agent?



