Trend Micro Deep-Security-Professional - Trend Micro Certified Professional for Deep Security Exam
Page: 3 / 3
Total 73 questions
Total 73 questions
What is the purpose of the override.properties file?
A Deep Security administrator wishes to monitor a Windows SQL Server database and be alerted of any critical events which may occur on that server. How can this be achieved using Deep Security?
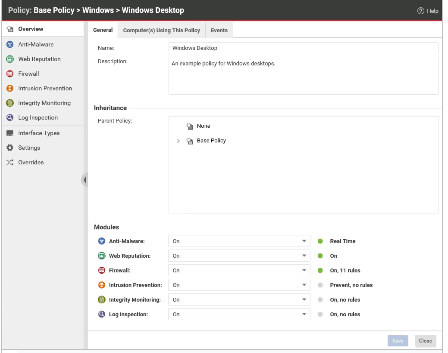
When viewing the details for a policy, as displayed in the exhibit, you notice that the Application Control Protection Module is not available. In this example, why would this Protection Modules not be available?
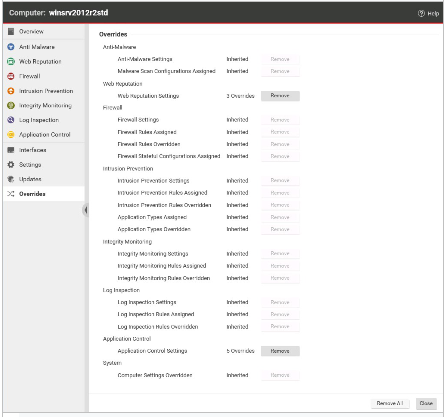
The Overrides settings for a computer are displayed in the exhibit. Which of the following statements is true regarding the displayed configuration?