ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
When discussing passwords, what is considered a brute force attack?
Which of the following statements about a zone transfer correct?(Choose three.
Jason's Web server was attacked by a trojan virus. He runs protocol analyzer and notices that the trojan communicates to a remote server on the Internet. Shown below is the standard "hexdump" representation of the network packet, before being decoded. Jason wants to identify the trojan by looking at the destination port number and mapping to a trojan-port number database on the Internet. Identify the remote server's port number by decoding the packet?
What hacking attack is challenge/response authentication used to prevent?
What is the goal of a Denial of Service Attack?
What is a Trojan Horse?
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
E-mail scams and mail fraud are regulated by which of the following?
Study the snort rule given below:
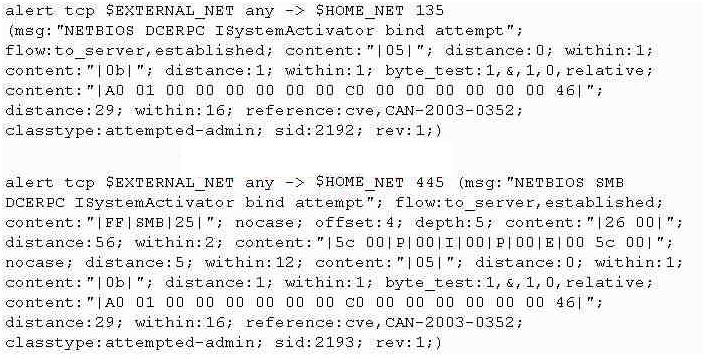
From the options below, choose the exploit against which this rule applies.
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
You are attempting to crack LM Manager hashed from Windows 2000 SAM file. You will be using LM Brute force hacking tool for decryption.
What encryption algorithm will you be decrypting?
A zone file consists of which of the following Resource Records (RRs)?
_____ is the process of converting something from one representation to the simplest form. It deals with the way in which systems convert data from one form to another.
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
You suspect that your Windows machine has been compromised with a Trojan virus. When you run anti-virus software it does not pick of the Trojan. Next you run netstat command to look for open ports and you notice a strange port 6666 open.
What is the next step you would do?
Exhibit:
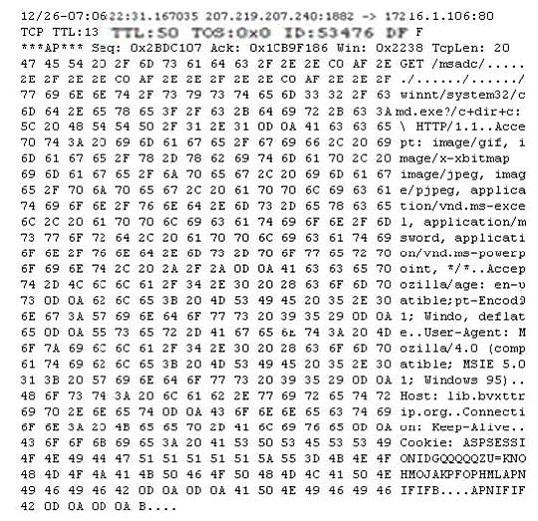
Study the following log extract and identify the attack.
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Tess King is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc) for a Domain. What do you think Tess King is trying to accomplish? Select the best answer.



