ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems. However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
What file system vulnerability does the following command take advantage of?
type c:\anyfile.exe > c:\winnt\system32\calc.exe:anyfile.exe
Exhibit:
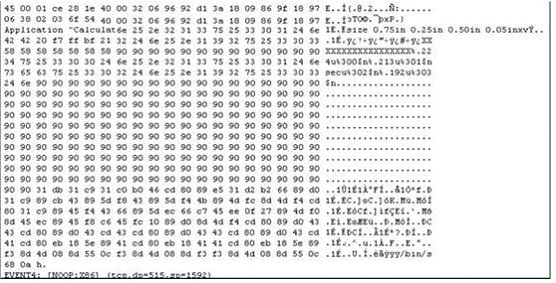
The following is an entry captured by a network IDS.You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?
This kind of password cracking method uses word lists in combination with numbers and special characters:
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap�
What is GINA?
Assuring two systems that are using IPSec to protect traffic over the internet, what type of general attack could compromise the data?
Sniffing is considered an active attack.
One of your junior administrator is concerned with Windows LM hashes and password cracking. In your discussion with them, which of the following are true statements that you would point out?
Select the best answers.
LM authentication is not as strong as Windows NT authentication so you may want to disable its use, because an attacker eavesdropping on network traffic will attack the weaker protocol. A successful attack can compromise the user's password. How do you disable LM authentication in Windows XP?
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
Take a look at the following attack on a Web Server using obstructed URL:
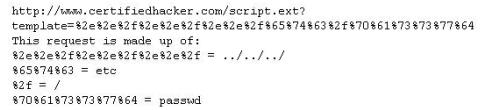
How would you protect from these attacks?
In which step Steganography fits in CEH System Hacking Cycle (SHC)
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
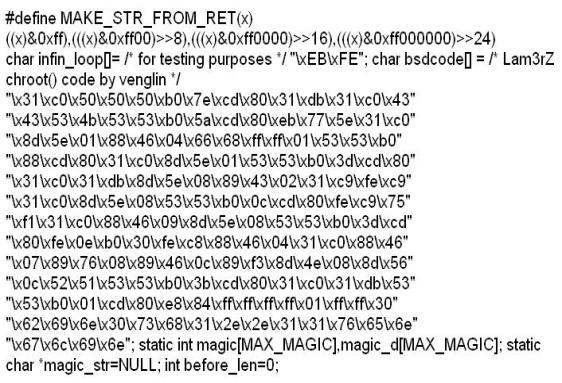
What can he infer from this file?
User which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
What port scanning method is the most reliable but also the most detectable?
Harold is the senior security analyst for a small state agency in New York. He has no other security professionals that work under him, so he has to do all the security-related tasks for the agency. Coming from a computer hardware background, Harold does not have a lot of experience with security methodologies and technologies, but he was the only one who applied for the position. Harold is currently trying to run a Sniffer on the agency's network to get an idea of what kind of traffic is being passed around, but the program he is using does not seem to be capturing anything. He pours through the Sniffer's manual, but cannot find anything that directly relates to his problem. Harold decides to ask the network administrator if he has any thoughts on the problem. Harold is told that the Sniffer was not working because the agency's network is a switched network, which cannot be sniffed by some programs without some tweaking. What technique could Harold use to sniff his agency's switched network?
To what does “message repudiation†refer to what concept in the realm of email security?
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool “SIDExtractorâ€. Here is the output of the SIDs:
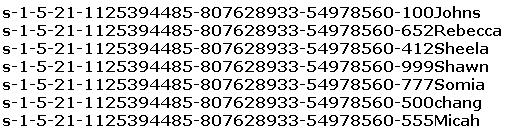
From the above list identify the user account with System Administrator privileges.
What is the proper response for a FIN scan if the port is closed?



