ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
An attacker has captured a target file that is encrypted with public key cryptography. Which of the attacks below is likely to be used to crack the target file?
There is a WEP encrypted wireless access point (AP) with no clients connected. In order to crack the WEP key, a fake authentication needs to be performed. What information is needed when performing fake authentication to an AP? (Choose two.)
What is a successful method for protecting a router from potential smurf attacks?
How can rainbow tables be defeated?
Clive is conducting a pen-test and has just port scanned a system on the network. He has identified the operating system as Linux and been able to elicit responses from ports 23, 25 and 53. He infers port 23 as running Telnet service, port 25 as running SMTP service and port 53 as running DNS service. The client confirms these findings and attests to the current availability of the services. When he tries to telnet to port 23 or 25, he gets a blank screen in response. On typing other commands, he sees only blank spaces or underscores symbols on the screen. What are you most likely to infer from this?
Exhibit:
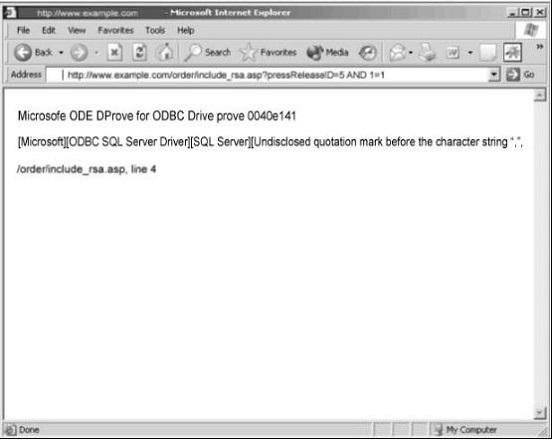
You are conducting pen-test against a company’s website using SQL Injection techniques. You enter “anuthing or 1=1-“ in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
What is the key advantage of Session Hijacking?
Sandra is conducting a penetration test for XYZ.com. She knows that XYZ.com is using wireless networking for some of the offices in the building right down the street. Through social engineering she discovers that they are using 802.11g. Sandra knows that 802.11g uses the same 2.4GHz frequency range as 802.11b. Using NetStumbler and her 802.11b wireless NIC, Sandra drives over to the building to map the wireless networks. However, even though she repositions herself around the building several times, Sandra is not able to detect a single AP.
What do you think is the reason behind this?
What is the tool Firewalk used for?
Which of the following is NOT a reason 802.11 WEP encryption is vulnerable?
You are doing IP spoofing while you scan your target. You find that the target has port 23 open. Anyway you are unable to connect. Why?
Once an intruder has gained access to a remote system with a valid username and password, the attacker will attempt to increase his privileges by escalating the used account to one that has increased privileges. such as that of an administrator. What would be the best countermeasure to protect against escalation of priveges?
Which is the right sequence of packets sent during the initial TCP three way handshake?
All the web servers in the DMZ respond to ACK scan on port 80. Why is this happening ?
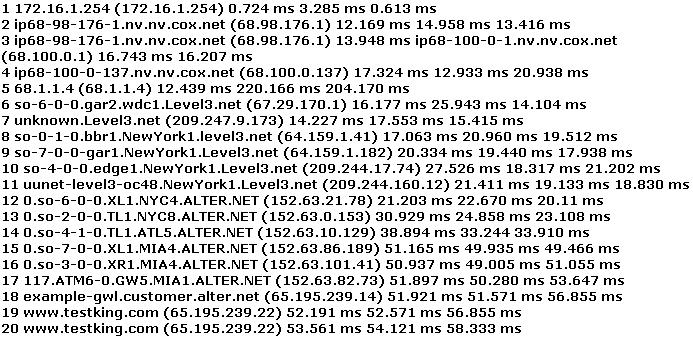
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?
Matthew re-injects a captured wireless packet back onto the network. He does this hundreds of times within a second. The packet is correctly encrypted and Matthew assumes it is an ARP request packet. The wireless host responds with a stream of responses, all individually encrypted with different IVs. What is this attack most appropriately called?
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered. What do you recommend?
Select the best answer.
Tess King is making use of Digest Authentication for her Web site. Why is this considered to be more secure than Basic authentication?
When referring to the Domain Name Service, what is denoted by a ‘zone’?



