ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
A program that defends against a port scanner will attempt to:
Bart is looking for a Windows NT/2000/XP command-line tool that can be used to assign, display, or modify ACL’s (access control lists) to files or folders and also one that can be used within batch files.
Which of the following tools can be used for that purpose? (Choose the best answer)
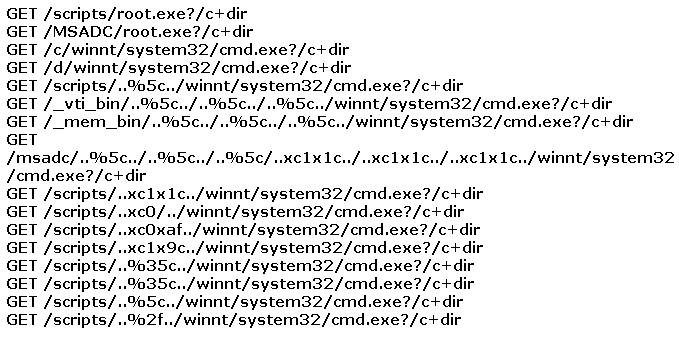
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe.
What caused this?
If you come across a sheepdip machaine at your client site, what would you infer?
On wireless networks, SSID is used to identify the network. Why are SSID not considered to be a good security mechanism to protect a wireless networks?
To scan a host downstream from a security gateway, Firewalking:
When working with Windows systems, what is the RID of the true administrator account?
Which of the following buffer overflow exploits are related to Microsoft IIS web server? (Choose three)
Eve decides to get her hands dirty and tries out a Denial of Service attack that is relatively new to her. This time she envisages using a different kind of method to attack Brownies Inc. Eve tries to forge the packets and uses the broadcast address. She launches an attack similar to that of fraggle. What is the technique that Eve used in the case above?
While scanning a network you observe that all of the web servers in the DMZ are responding to ACK packets on port 80.
What can you infer from this observation?
This packet was taken from a packet sniffer that monitors a Web server.

This packet was originally 1514 bytes long, but only the first 512 bytes are shown here. This is the standard hexdump representation of a network packet, before being decoded. A hexdump has three columns: the offset of each line, the hexadecimal data, and the ASCII equivalent. This packet contains a 14-byte Ethernet header, a 20-byte IP header, a 20-byte TCP header, an HTTP header ending in two line-feeds (0D 0A 0D 0A) and then the data. By examining the packet identify the name and version of the Web server?
Bill is attempting a series of SQL queries in order to map out the tables within the database that he is trying to exploit.
Choose the attack type from the choices given below.
What is Hunt used for?
Jane has just accessed her preferred e-commerce web site and she has seen an item she would like to buy. Jane considers the price a bit too steep; she looks at the page source code and decides to save the page locally to modify some of the page variables. In the context of web application security, what do you think Jane has changed?
A particular database threat utilizes a SQL injection technique to penetrate a target system. How would an attacker use this technique to compromise a database?
Which of the following statements best describes the term Vulnerability?
What is a primary advantage a hacker gains by using encryption or programs such as Loki?
You are the security administrator for a large network. You want to prevent attackers from running any sort of traceroute into your DMZ and discover the internal structure of publicly accessible areas of the network.
How can you achieve this?
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
A company has hired a security administrator to maintain and administer Linux and Windows-based systems. Written in the nightly report file is the followinG.
Firewall log files are at the expected value of 4 MB. The current time is 12am. Exactly two hours later the size has decreased considerably. Another hour goes by and the log files have shrunk in size again.
Which of the following actions should the security administrator take?



