ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
A Network Administrator was recently promoted to Chief Security Officer at a local university. One of employee's new responsibilities is to manage the implementation of an RFID card access system to a new server room on campus. The server room will house student enrollment information that is securely backed up to an off-site location.
During a meeting with an outside consultant, the Chief Security Officer explains that he is concerned that the existing security controls have not been designed properly. Currently, the Network Administrator is responsible for approving and issuing RFID card access to the server room, as well as reviewing the electronic access logs on a weekly basis.
Which of the following is an issue with the situation?
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
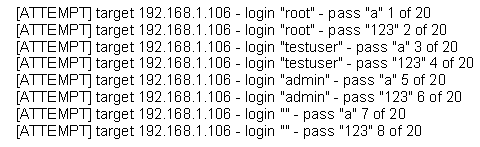
What is most likely taking place?
An NMAP scan of a server shows port 69Â is open. What risk could this pose?
Which of the following tools would be the best choice for achieving compliance with PCI Requirement 11?
What are common signs that a system has been compromised or hacked? (Choose three.)
The network administrator for a company is setting up a website with e-commerce capabilities. Packet sniffing is a concern because credit card information will be sent electronically over the Internet. Customers visiting the site will need to encrypt the data with HTTPS. Which type of certificate is used to encrypt and decrypt the data?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
Which of the following is a component of a risk assessment?
While performing data validation of web content, a security technician is required to restrict malicious input. Which of the following processes is an efficient way of restricting malicious input?
Which statement best describes a server type under an N-tier architecture?
A recently hired network security associate at a local bank was given the responsibility to perform daily scans of the internal network to look for unauthorized devices. The employee decides to write a script that will scan the network for unauthorized devices every morning at 5:00 am.
Which of the following programming languages would most likely be used?
An IT security engineer notices that the company’s web server is currently being hacked. What should the engineer do next?
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
Which of the following cryptography attack methods is usually performed without the use of a computer?
Which of the following describes the characteristics of a Boot Sector Virus?
Which of the following algorithms provides better protection against brute force attacks by using a 160-bit message digest?
Which security strategy requires using several, varying methods to protect IT systems against attacks?
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
A tester has been hired to do a web application security test. The tester notices that the site is dynamic and must make use of a back end database.
In order for the tester to see if SQL injection is possible, what is the first character that the tester should use to attempt breaking a valid SQL request?
Which of the following examples best represents a logical or technical control?



