ECCouncil EC0-350 - Ethical Hacking and Countermeasures V8
Botnets are networks of compromised computers that are controlled remotely and surreptitiously by one or more cyber criminals. How do cyber criminals infect a victim's computer with bots? (Select 4 answers)
Which of the following is optimized for confidential communications, such as bidirectional voice and video?
MX record priority increases as the number increases. (True/False.
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately.
Which organization coordinates computer crime investigations throughout the United States?
What is "Hacktivism"?
What are two types of ICMP code used when using the ping command?
Network Administrator Patricia is doing an audit of the network. Below are some of her findings concerning DNS. Which of these would be a cause for alarm?
Select the best answer.
A company is legally liable for the content of email that is sent from its systems, regardless of whether the message was sent for private or business-related purposes. This could lead to prosecution for the sender and for the company's directors if, for example, outgoing email was found to contain material that was pornographic, racist, or likely to incite someone to commit an act of terrorism. You can always defend yourself by "ignorance of the law" clause.
A XYZ security System Administrator is reviewing the network system log files.
He notes the following:
Network log files are at 5 MB at 12:00 noon.
At 14:00 hours, the log files at 3 MB.
What should he assume has happened and what should he do about the situation?
Which of the following Nmap commands would be used to perform a stack fingerprinting?
One of your team members has asked you to analyze the following SOA record. What is the TTL?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.
Which of the following command line switch would you use for OS detection in Nmap?
What ICMP message types are used by the ping command?
Exhibit
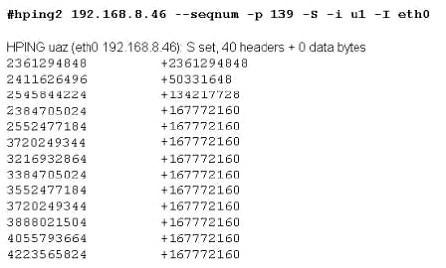
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
This is an example of whois record.
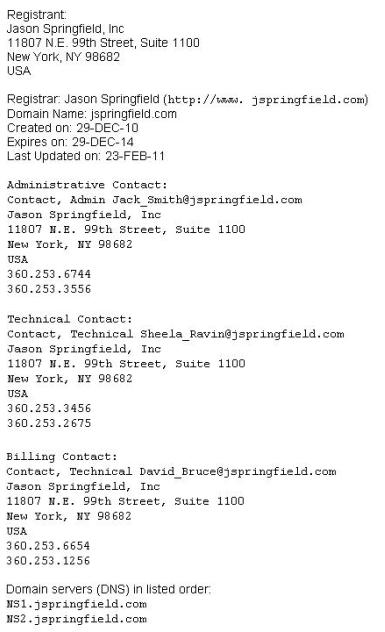
Sometimes a company shares a little too much information on their organization through public domain records. Based on the above whois record, what can an attacker do? (Select 2 answers)
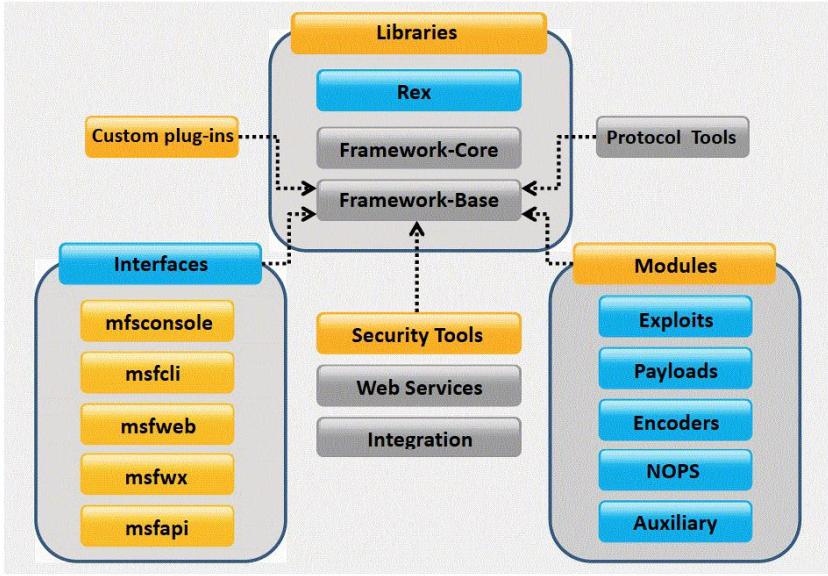
What framework architecture is shown in this exhibit?
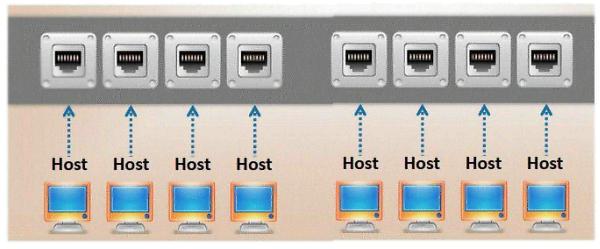
Which port, when configured on a switch receives a copy of every packet that passes through it?
Jason is the network administrator of Spears Technology. He has enabled SNORT IDS to detect attacks going through his network. He receives Snort SMS alerts on his iPhone whenever there is an attempted intrusion to his network.
He receives the following SMS message during the weekend.
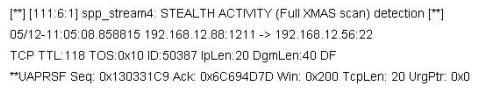
An attacker Chew Siew sitting in Beijing, China had just launched a remote scan on Jason's network with the hping command.
Which of the following hping2 command is responsible for the above snort alert?
Study the snort rule given below and interpret the rule.
alert tcp any any --> 192.168.1.0/24 111 (content:"|00 01 86 a5|"; msG. "mountd access";)
What is the IV key size used in WPA2?



