CyberArk EPM-DEF - CyberArk Defender - EPM
A company is looking to manage their Windows Servers and Desktops with CyberArk EPM. Management would like to define different default policies between the Windows Servers and Windows Desktops.
What should the EPM Administrator do?
What are the policy targeting options available for a policy upon creation?
After a clean installation of the EPM agent, the local administrator password is not being changed on macOS and the old password can still be used to log in.
What is a possible cause?
An end user is reporting that an application that needs administrative rights is crashing when selecting a certain option menu item. The Application is part of an advanced elevate policy and is working correctly except when using that menu item.
What could be the EPM cause of the error?
Can the EPM Set Administrator configure Audit Dialog Pop-ups for the Record Audit Video option?
How does a Trusted Source policy affect an application?
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation regarding the username creation?
Select the default threat intelligence source that requires additional licensing.
How does CyberArk EPM's Ransomware Protection feature monitor for Ransomware Attacks?
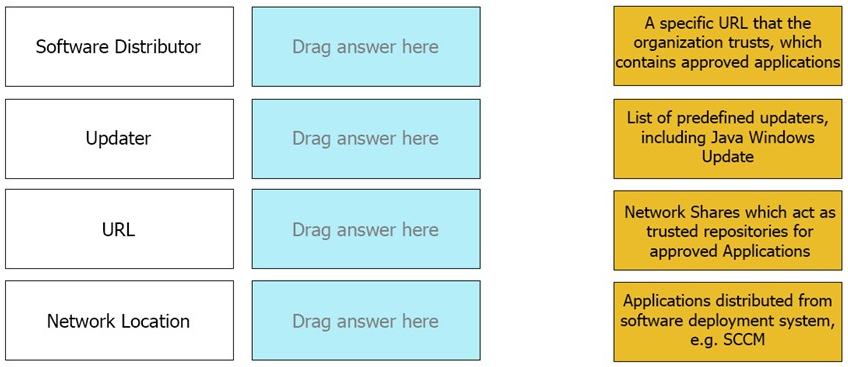
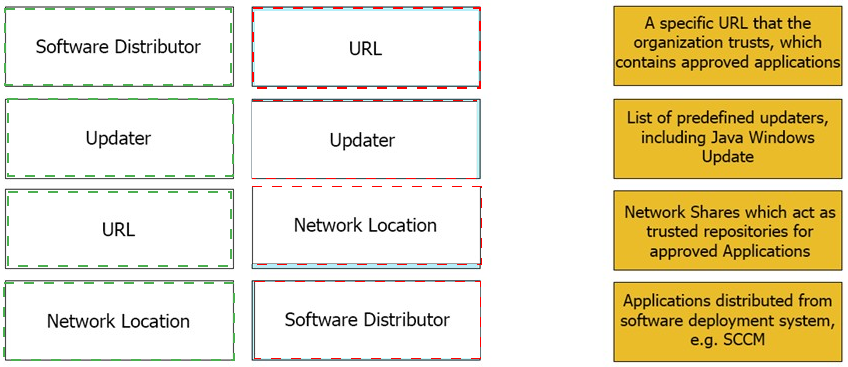
Match the Trusted Source to its correct definition: