Fortinet FCP_FGT_AD-7.6 - FortiGate 7.6 Administrator FCP_FGT_AD-7.6
Refer to the exhibit.
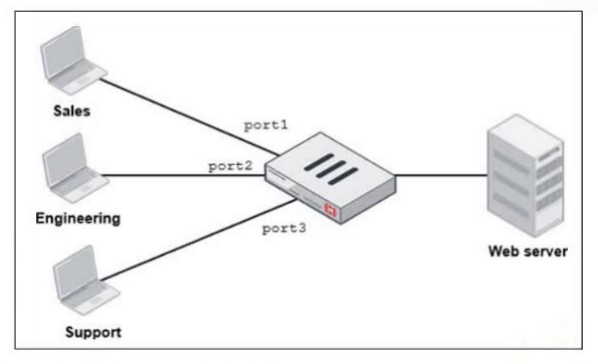
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
Refer to the exhibit.

The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
You are encountering connectivity problems caused by intermediate devices blocking IPsec traffic.
In which two ways can you effectively resolve the problem? (Choose two.)
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements about the requirements of connected physical interfaces on FortiGate are true? (Choose two.)
When configuring firewall policies which of the following is true regarding the policy ID?
Refer to the exhibits.
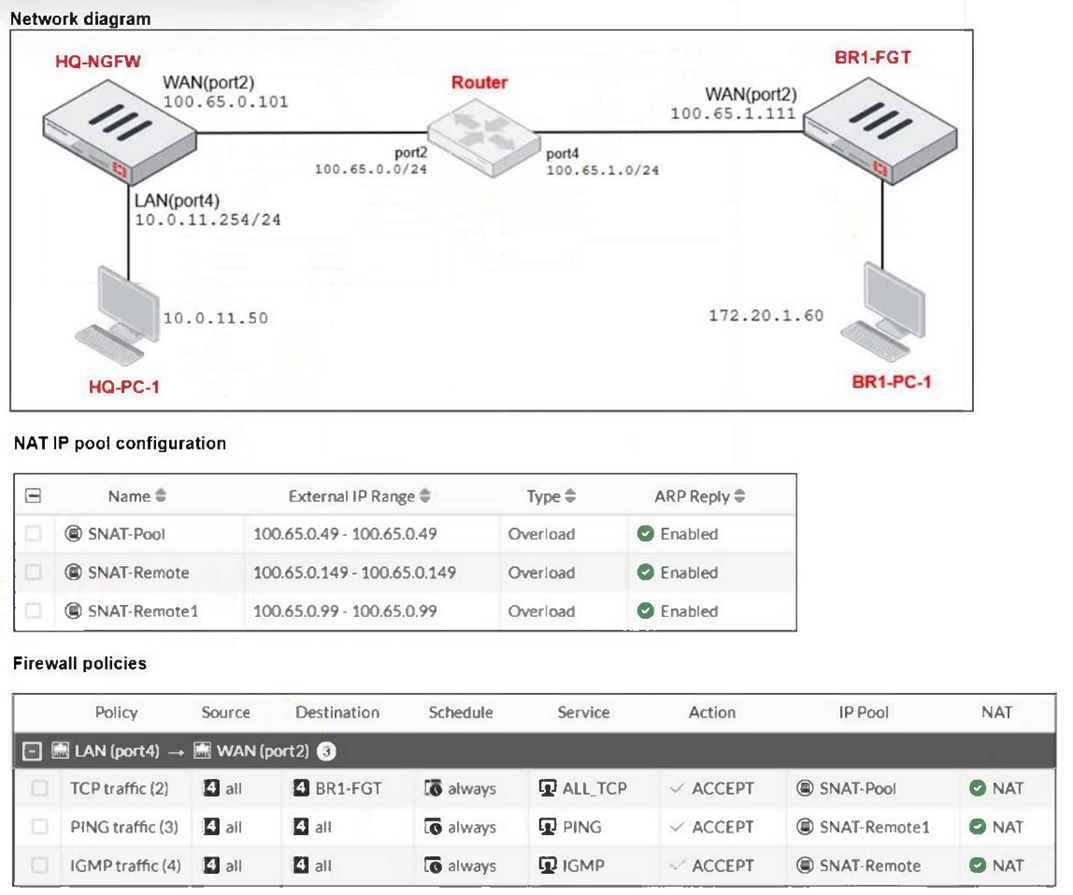
The exhibits show a diagram of a FortiGate device connected to the network, as well as the IP pool configuration and firewall policy objects.
The WAN (port2) interface has the IP address 100.65.0.101/24.
The LAN (port4) interface has the IP address 10.0.11.254/24.
Which IP address will be used to source NAT (SNAT) the traffic, if the user on
HQ-PC-1 (10.0.11.50) pings the IP address of BR-FGT (100.65.1.111)
Refer to the exhibit.
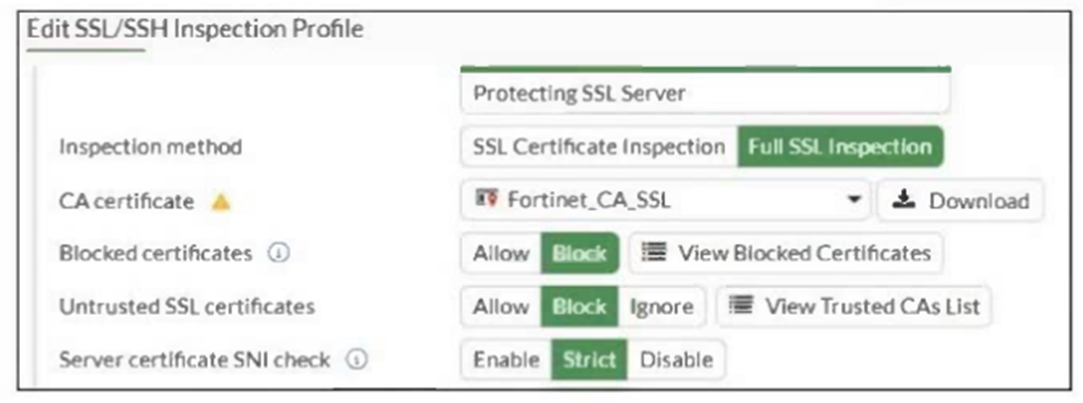
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.

Based on the exhibit, which statement is true?
Refer to the exhibits.
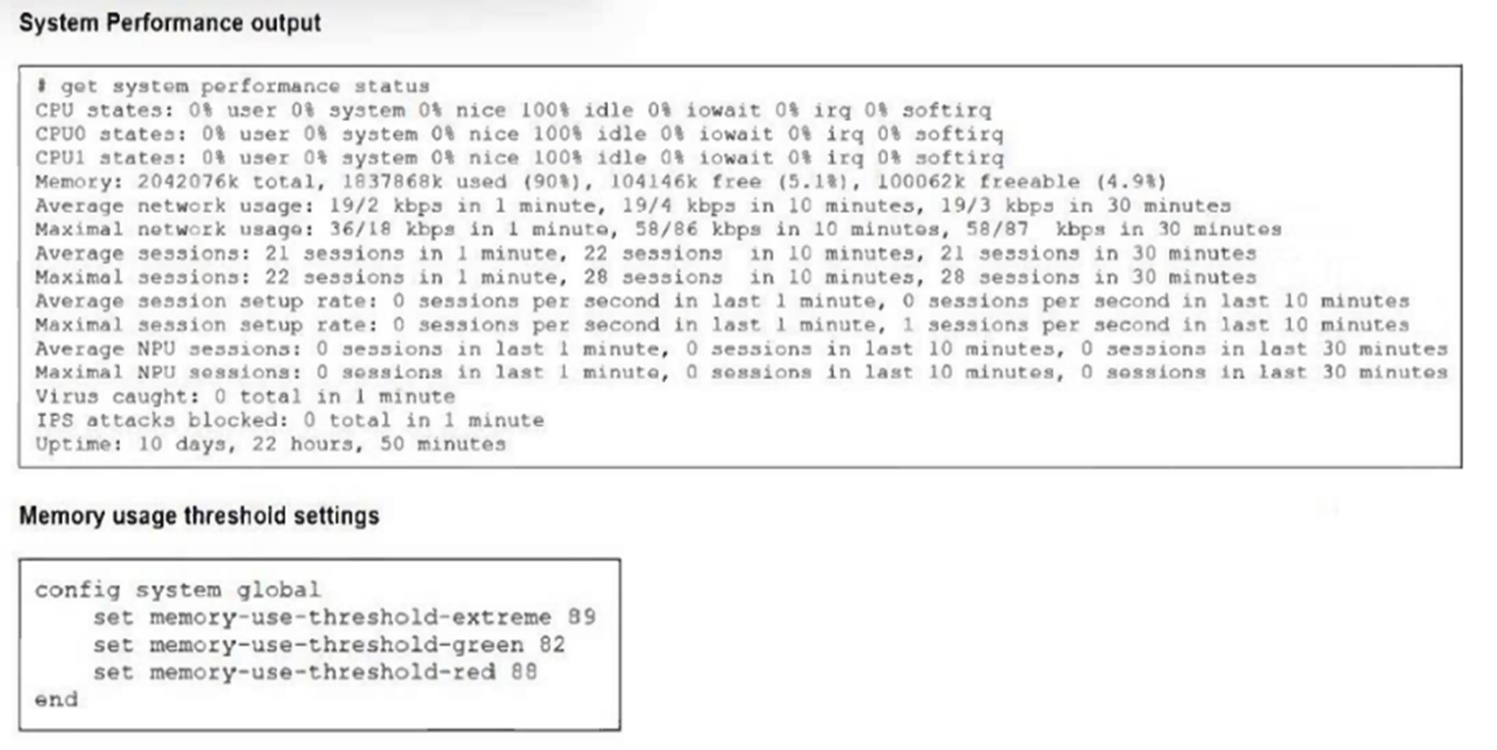
The exhibits show the system performance output and default configuration of high memory usage thresholds on a FortiGate device.
Based on the system performance output, what are the two possible outcomes? (Choose two.)



