Fortinet FCP_FML_AD-7.4 - FCP - FortiMail 7.4 Administrator
Refer to the exhibit, which shows a topology diagram of two MTAs.
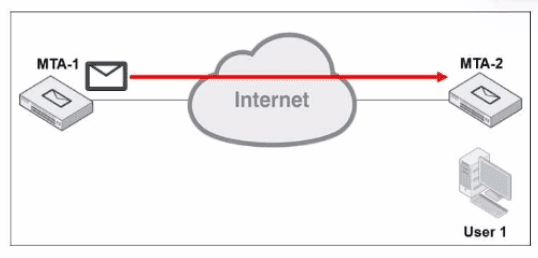
MTA-1 is delivering an email intended for User 1 to MTA-2. User 1 uses Outlook as an email client. Which two statements about protocol usage between these devices are correct? (Choose two.)
Refer to the exhibit, which shows the Authentication Reputation list on a FortiMail device running in gateway mode.
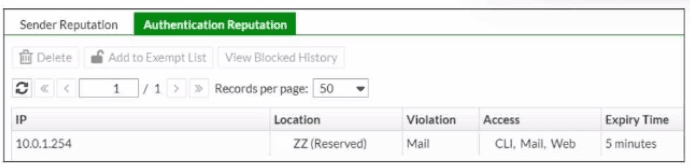
Why was the IP address blocked?
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identities that the DSNs were not generated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator enable to prevent this scenario?
A FortiMail device is configured with the protected domain example. com.
It senders are not authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
In which two ways does a transparent mode FortiMail use the build-it MTA to process email? (Choose two.)
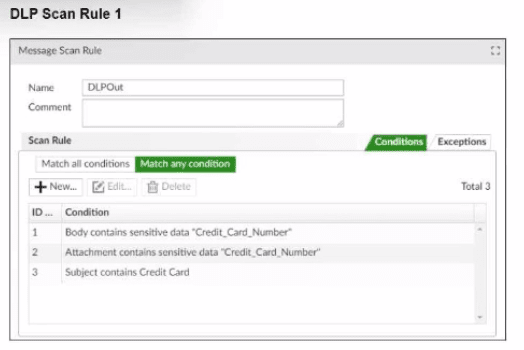
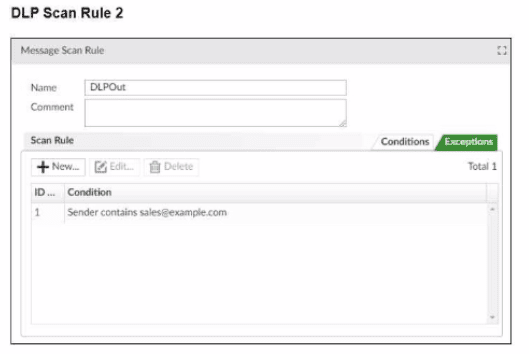
Refer to the exhibits, which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
Which two message types will trigger this DLP scan rule? (Choose two.)
Which item is a supported one-time secure token for IBE authentication?
Refer to the exhibit, which displays a history log entry.
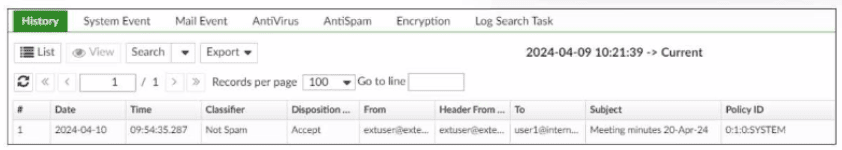
In the Policy ID column, why isthe last policy ID value SYSTEM?
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
Refer to the exhibits showing SMTP limits (Session Profile — SMTP Limits), and domain settings (Domain Settings, andDomain Settings — Other) of a FortiMail device.
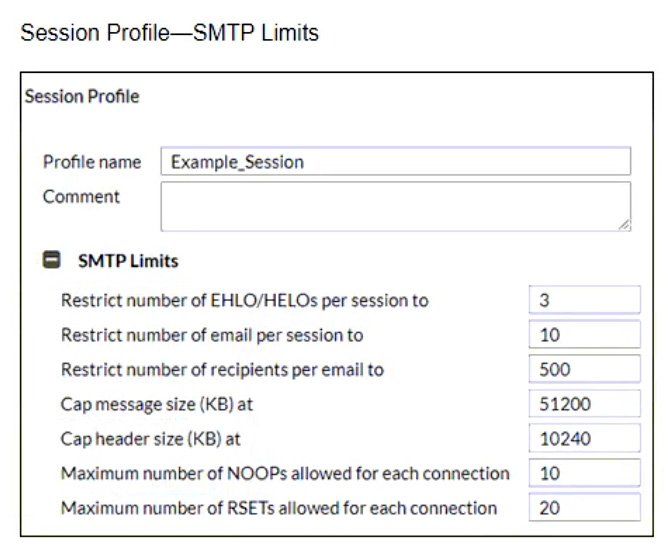
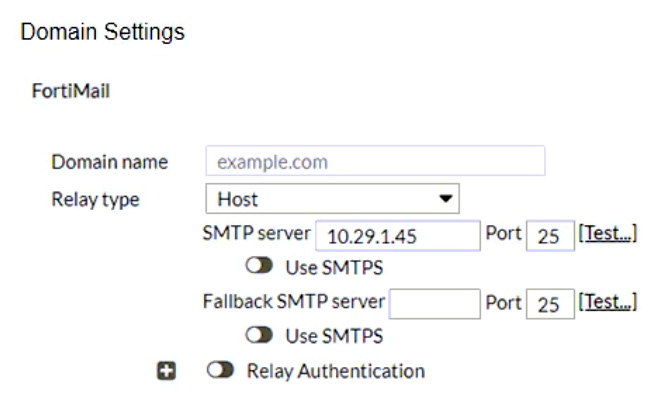
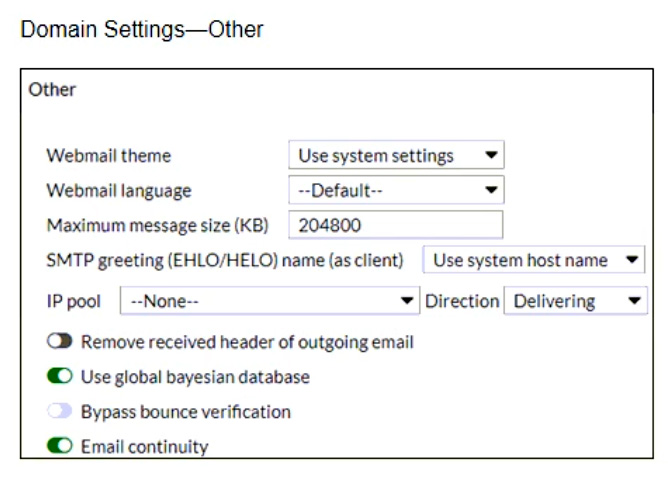
Which message size limit in KB will the FortiMail apply to outbound email?



