Fortinet FCSS_EFW_AD-7.6 - Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator
An administrator applied a block-all IPS profile for client and server targets to secure the server, but the database team reported the application stopped working immediately after.
How can an administrator apply IPS in a way that ensures it does not disrupt existing applications in the network?
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
An administrator is designing an ADVPN network for a large enterprise with spokes that have varying numbers of internet links. They want to avoid a high number of routes and peer connections at the hub.
Which method should be used to simplify routing and peer management?
A company's guest internet policy, operating in proxy mode, blocks access to Artificial Intelligence Technology sites using FortiGuard. However, a guest user accessed a page in this category using port 8443.
Which configuration changes are required for FortiGate to analyze HTTPS traffic on nonstandard ports like 8443 when full SSL inspection is active in the guest policy?
A FortiGate device with UTM profiles is reaching the resource limits, and the administrator expects the traffic in the enterprise network to increase.
The administrator has received an additional FortiGate of the same model.
Which two protocols should the administrator use to integrate the additional FortiGate device into this enterprise network? (Choose two.)
Refer to the exhibit, which shows a corporate network and a new remote office network.
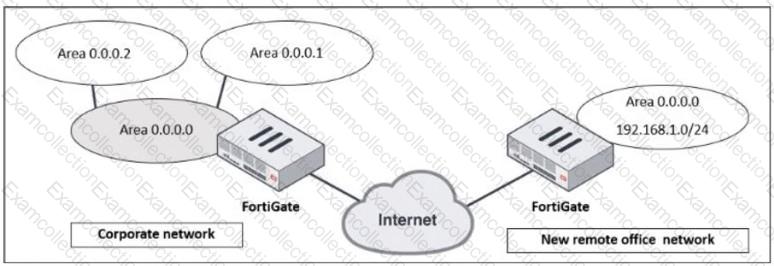
An administrator must integrate the new remote office network with the corporate enterprise network.
What must the administrator do to allow routing between the two networks?
Refer to the exhibit, which shows a physical topology and a traffic log.
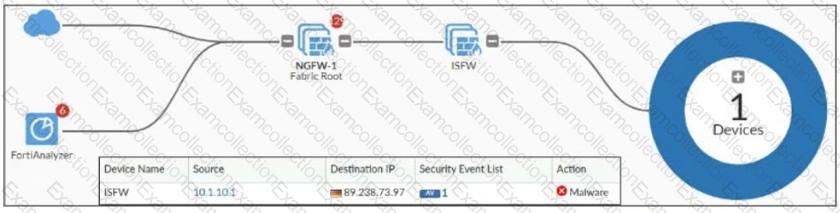
The administrator is checking on FortiAnalyzer traffic from the device with IP address 10.1.10.1, located behind the FortiGate ISFW device.
The firewall policy in on the ISFW device does not have UTM enabled and the administrator is surprised to see a log with the action Malware, as shown in the exhibit.
What are the two reasons FortiAnalyzer would display this log? (Choose two.)
During the maintenance window, an administrator must sniff all the traffic going through a specific firewall policy, which is handled by NP6 interfaces. The output of the sniffer trace provides just a few packets.
Why is the output of sniffer trace limited?
Refer to the exhibit, which contains a partial command output.

The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?



 FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster.
FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster. With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices.
With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices. This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls.
This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls. FGSP is effective when stateful failover is required but without the constraints of traditional HA.
FGSP is effective when stateful failover is required but without the constraints of traditional HA. FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency.
FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency. Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern.
Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern. Using switches ensures redundancy and avoids single points of failure in the network.
Using switches ensures redundancy and avoids single points of failure in the network. This mode is commonly used in enterprise networks where both scalability and redundancy are required.
This mode is commonly used in enterprise networks where both scalability and redundancy are required.