GIAC GCFW - GIAC Certified Firewall Analyst
Which of the following steps are generally followed in computer forensic examinations?
Each correct answer represents a complete solution. Choose three.
Which of the following proxy servers is also referred to as transparent proxies or forced proxies?
Which of the following attacking methods allows the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another computer by changing the Media Access Control address?
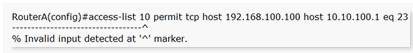
Choose the best explanation for the resulting error when entering the command below.
Which of the following tools can be used as a Linux vulnerability scanner that is capable of identifying operating systems and network services?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following IPv4 to IPv6 transition methods uses encapsulation of IPv6 packets to traverse IPv4 networks?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. In order to do so, he performs the following steps of the preattack phase successfully:
l Information gathering
l Determination of network range
l Identification of active systems
l Location of open ports and applications
Now, which of the following tasks should he perform next?
Which of the following types of firewall ensures that the packets are part of the established session?
Which of the following firewalls operates at three layers- Layer3, Layer4, and Layer5?
Which of the following tools is used to analyze the files produced by several popular packetcapture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?



