GIAC GCFW - GIAC Certified Firewall Analyst
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the default port for POP3?
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008- based network. You have created a test domain for testing IPv6 addressing. Which of the following types of addresses are supported by IPv6?
Each correct answer represents a complete solution. Choose all that apply.
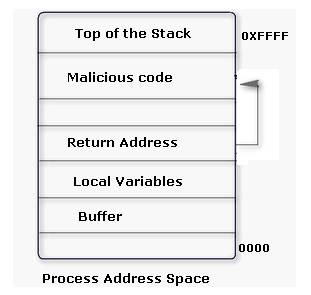
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
Which of the following tools can be used as a countermeasure to such an attack?
A remote-access VPN offers secured and encrypted connections between mobile or remote users and their corporate network across public networks. Which of the following does the remote-access VPN use for offering these types of connections?
Each correct answer represents a complete solution. Choose two.
Which of the following wireless security features provides the best wireless security mechanism?
Peter works as a Computer Hacking Forensic Investigator. He has been called by an organization to conduct a seminar to give necessary information related to sexual harassment within the work place. Peter started with the definition and types of sexual harassment. He then wants to convey that it is important that records of the sexual harassment incidents should be maintained, which helps in further legal prosecution. Which of the following data should be recorded in this documentation?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Which of the following types of IP actions are supported by an IDP rulebase?



