GIAC GCIA - GCIA – GIAC Certified Intrusion Analyst Practice Test
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection.
He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?
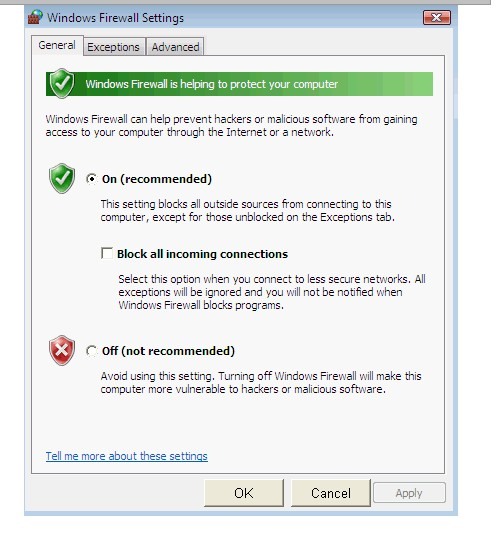
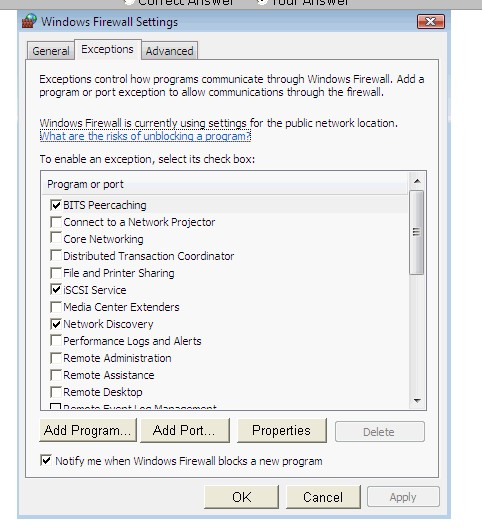
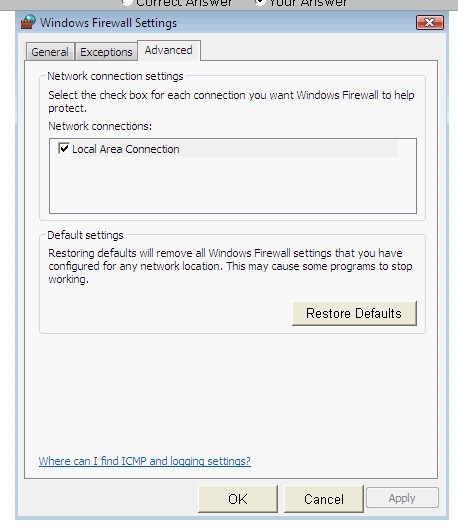
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system and wants to install an Intrusion Detection System on the We-are-secure server so that he can receive alerts about any hacking attempts. Which of the following tools can John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned a project for testing the security of www.we-are-secure.com. He scans the We-are-secure server and gets the following result:
sysDescr.0 = STRING. "SunOS we-are-secure.com 4.1.3_U1 1 sun4m"
sysObjectID.0 = OID. enterprises.hp.nm.hpsystem.10.1.1
sysUpTime.0 = Timeticks: (156474552) 18 days, 12:00:09
sysContact.0 = STRING. ""
sysName.0 = STRING. "we-are-secure.com"
sysLocation.0 = STRING. ""
sysServices.0 = INTEGER: 6
Which of the following tools is John using to perform the scan?
The Intrusion Detection System (IDS) instructs the firewall to reject any request from a particular IP address if the network is repeatedly attacked from this address. What is this action known as?
At which port does a DHCPv6 client listen for DHCP messages?
Which of the following tools is used to locate lost files and partitions to restore data from a formatted, damaged, or lost partition in Windows and Apple Macintosh computers?
Which of the following attacks is based on the concept that IDSs cannot recognize Unicode encoded malicious data?
Which of the following is an example of a firewall?
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. You are configuring an Internet connection on a server. Which of the following servers filters outbound Web traffic on the network?
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple small-sized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is an open source network intrusion prevention and detection system that operates as a network sniffer?
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?



