GIAC GCIA - GCIA – GIAC Certified Intrusion Analyst Practice Test
Ryan, a malicious hacker submits Cross-Site Scripting (XSS) exploit code to the Website of Internet forum for online discussion. When a user visits the infected Web page, code gets automatically executed and Ryan can easily perform acts like account hijacking, history theft etc. Which of the following types of Cross-Site Scripting attack Ryan intends to do?
Which of the following classes refers to the fire involving electricity?
Peter works as a System Administrator for TechSoft Inc. The company uses Linux-based systems.
Peter's manager suspects that someone is trying to log in to his computer in his absence. Which of the following commands will Peter run to show the last unsuccessful login attempts, as well as the users who have last logged in to the manager's system?
Each correct answer represents a complete solution. Choose two.
Which of the following commands displays the IPX routing table entries?
Which of the following IP packet elements is responsible for authentication while using IPSec?
Which of the following is computed from an arbitrary block of digital data for the purpose of detecting accidental errors?
Which of the following distributes incorrect IP address to divert the traffic?
Which of the following software is used for Steganography?
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
In which of the following IDS evasion attacks does an attacker send a data packet such that IDS accepts the data packet but the host computer rejects it?
Which of the following is a form of cheating or copying someone else's work or idea without acknowledging the source?
Which of the following is the process of categorizing attack alerts produced from an IDS in order to distinguish false positives from actual attacks?
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008- based network. You have created a test domain for testing IPv6 addressing. Which of the following types of addresses are supported by IPv6?
Each correct answer represents a complete solution. Choose all that apply.
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
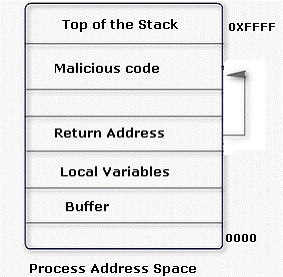
Which of the following tools can be used as a countermeasure to such an attack?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a compromised system of a cyber criminal, who hides some information in his computer. This computer runs on Linux operating system. Adam wants to extract the data units of a file, which is specified by its meta-data address. He is using the Sleuth Kit for this purpose. Which of the following commands in the Sleuth kit will he use to accomplish the task?



