GIAC GCIA - GCIA – GIAC Certified Intrusion Analyst Practice Test
Which of the following Denial-of-Service (DoS) attacks employ IP fragmentation mechanism?
Each correct answer represents a complete solution. Choose two.
Adam works as a Security Administrator for Umbrella. A project has been assigned to him to test the network security of the company. He created a webpage to discuss the progress of the tests with employees who were interested in following the test. Visitors were allowed to click on a company's icon to mark the progress of the test. Adam successfully embeds a keylogger. He also added some statistics on the webpage. The firewall protects the network well and allows strict Internet access.
How was security compromised and how did the firewall respond?
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration.
The tool uses raw IP packets to determine the following:
What ports are open on our network systems.
What hosts are available on the network.
Identify unauthorized wireless access points.
What services (application name and version) those hosts are offering.
What operating systems (and OS versions) they are running.
What type of packet filters/firewalls are in use.
Which of the following tools is Victor using?
What are the limitations of the POP3 protocol?
Each correct answer represents a complete solution. Choose three.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate and examine drive image of a compromised system, which is suspected to be used in cyber crime. Adam uses Forensic Sorter to sort the contents of hard drive in different categories. Which of the following type of image formats is NOT supported by Forensic Sorter?
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple smallsized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools works by using standard set of MS-DOS commands and can create an MD5 hash of an entire drive, partition, or selected files?
John works as a Security Administrator for NetPerfect Inc. The company uses Windows-based systems. A project has been assigned to John to track malicious hackers and to strengthen the company's security system. John configures a computer system to trick malicious hackers into thinking that it is the company's main server, which in fact is a decoy system to track hackers.
Which system is John using to track the malicious hackers?
Which of the following is the default port for TACACS?
When no anomaly is present in an Intrusion Detection, but an alarm is generated, the response is known as __________.
Ben works as a Network Administrator in Business Software Solutions Ltd. The company uses a Windowsbased operating system throughout its network. Ben finds the following mail exchange record on the server:
max1.passguide.com. IN A 613.0.2.1
IN AAAA 4ffe:d00:1:1::88
Which of the following conclusions can Ben derive from this record?
Which of the following firewalls operates at three layers- Layer3, Layer4, and Layer5?
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - ->
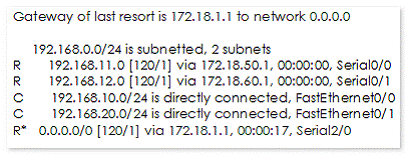
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?



