GIAC GPEN - GIAC Penetration Tester
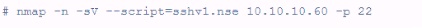
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command?
Which of the following best explains why you would warn to clear browser slate (history. cache, and cookies) between examinations of web servers when you've been trapping and altering values with a non-transparent proxy?
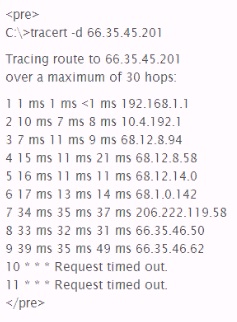
What is the most likely cause of the responses on lines 10 and 11 of the output below?
Where are Netcat's own network activity messages, such as when a connection occurs, sent?
All of the following are advantages of using the Metasploitpriv module for dumping hashes from a local Windows machine EXCEPT:
You are performing a vulnerability assessment using Nessus and your clients printers begin printing pages of random text and showing error messages. The client is not happy with the situation. What is the best way to proceed?
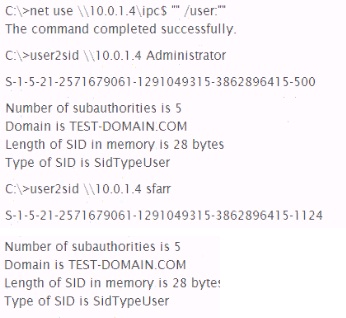
Analyze the command output below. What action is being performed by the tester?
You are conducting a penetration test for a private contractor located in Singapore. The scope extends to all internal hosts controlled by the company, you have gathered necessary hold-harmless and nondisclosure agreements. Which action by your group can incur criminal liability under Chapter 50a, Computer Misuse Act?
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
What is the purpose of the following command?
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]



