GIAC GPEN - GIAC Penetration Tester
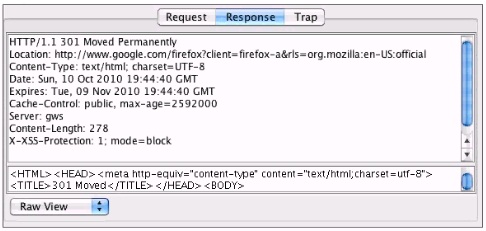
You've been asked to test a non-transparent proxy lo make sure it is working. After confirming the browser is correctly pointed at the proxy, you try to browse a web site. The browser indicates it is "loading" but never displays any part the page. Checking the proxy, you see a valid request in the proxy from your browser. Checking the response to the proxy, you see the results displayed in the accompanying screenshot. Which of the following answers is the most likely reason the browser hasn't displayed the page yet?
Which Metasploitvncinject stager will allow VNC communications from the attacker to a listening port of the attacker's choosing on the victim machine?
What section of the penetration test or ethical hacking engagement final report is used to detail and prioritize the results of your testing?
Your company has decided that the risk of performing a penetration test Is too great. You would like to figure out other ways to find vulnerabilities on their systems, which of the following is MOST likely to be a valid alternative?
When DNS is being used for load balancing, why would a penetration tester choose to identify a scan target by its IP address rather than its host name?
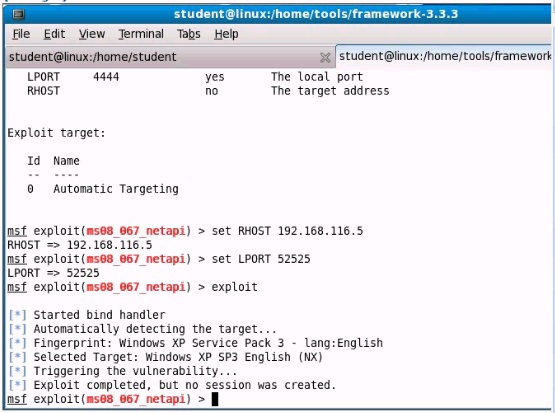
Analyze the screenshot below. What event is depicted?
As pan or a penetration lest, your team is tasked with discovering vulnerabilities that could be exploited from an inside threat vector. Which of the following activities fall within that scope?
By default Active Directory Controllers store password representations in which file?
You work as an IT Technician for uCertify Inc. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
Adam, a malicious hacker, hides a hacking tool from a system administrator of his company by using Alternate Data Streams (ADS) feature. Which of the following statements is true in context with the above scenario?



