GIAC GPEN - GIAC Penetration Tester
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
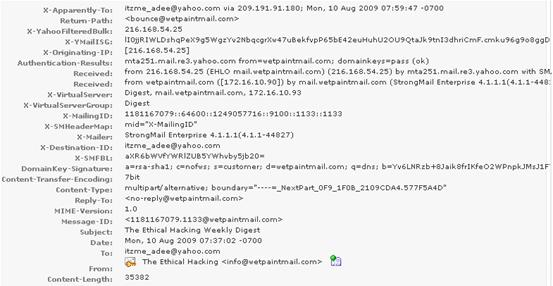
What is the IP address of the sender of this email?
Which of the following ports must you filter to check null sessions on your network?
You are a Web Administrator of Millennium Inc. The company has hosted its Web site within its network. The management wants the company's vendors to be able to connect to the corporate site from their locations through the Internet. As a public network is involved in this process, you are concerned about the security of data transmitted between the vendors and the corporate site.
Which of the following can help you?
Which of the following characters will you use to check whether an application is vulnerable to an SQL injection attack?
Which of the following can be used to mitigate the evil twin phishing attack?
When you conduct the XMAS scanning using Nmap, you find that most of the ports scanned do not give a response. What can be the state of these ports?
Which of the following password cracking tools can work on the Unix and Linux environment?
You want to retrieve the default security report of nessus. Which of the following google search queries will you use?
You want to perform passive footprinting against we-are-secure Inc. Web server. Which of the following tools will you use?



