GIAC GSLC - GIAC Security Leadership Certification (GSLC)
You work as a Software Developer for PassGuide Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. You use the application to create an assembly. Now you need to encrypt assembly data. The company has not provided encryption requirements to you. Which of the following symmetric cryptography classes will you use to accomplish this task?
You are the program manager for your project. You are working with the project managers regarding the procurement processes for their projects. You have ruled out one particular contract type because it is considered too risky for the program. Which one of the following contract types is usually considered to be the most dangerous for the buyer?
Which of the following documents is described in the statement below?
"It is developed along with all processes of the risk management. It contains the results of the qualitative risk analysis, quantitative risk analysis, and risk response planning."
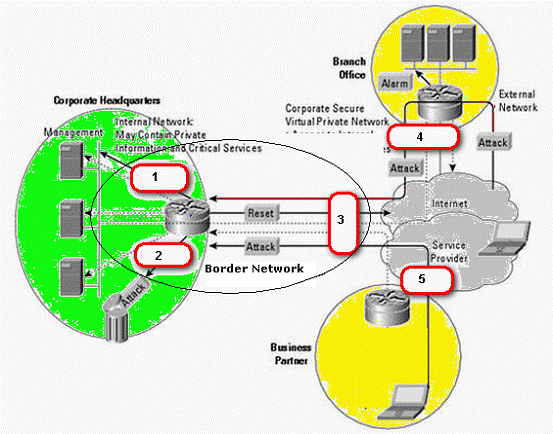
You work as a Security manager for Caterxiss Inc. The headquarters of your company is connected to the branch office in another state and a service partner in the same state. The network of the company is being attacked from the connected networks. You decide to analyze and then prevent the corporate headquarters network from these attacks using a Snort IDS.
What is the most appropriate spot on the network where you should set up an Intrusion detection system (IDS)?
Joseph works as a Network Administrator for WebTech Inc. He has to set up a centralized area on the network so that each employee can share resources and documents with one another. Which of the following will he configure to accomplish the task?
PassGuide Research and Training Center is developing its new network model. Which of the following protocols should be implemented in the new network? (Click the Exhibit button on the toolbar to see the case study.) Each correct answer represents a complete solution. Choose two.
A helpdesk technician received a phone call from an administrator at a remote branch office. The administrator claimed to have forgotten the password for the root account on UNIX servers and asked for it. Although the technician didn't know any administrator at the branch office, the guy sounded really friendly and since he knew the root password himself, he supplied the caller with the password.
What type of attack has just occurred?
Which of the following methods can be helpful to eliminate social engineering threat?
Each correct answer represents a complete solution. Choose three.
You are writing the change management plan for your upcoming project. You want to address mistakes that could happen during the execution of the project. Your change management plan requires the project team to correct any errors that deviate from the project scope as an error is technically an unapproved scope change. What else should you address in regard to errors in project team execution?
You work as a Software Developer for PassGuide Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
A project team member has just identified a new project risk. The risk event is determined to have significant impact but a low probability in the project. Should the risk event happen it'll cause the project to be delayed by three weeks, which will cause new risk in the project. What should the project manager do with the risk event?
The Project Scope Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
Your project is to implement a new operating system for all of the workstations in your company's network. Every workstation must have the new operating system as part of an organization-wide mandate. Many users are not happy with this decision and are resisting the change. Some of the users are complaining that they do not want the operating system at all. What type of stakeholders are these users?



