GIAC GSNA - GIAC Systems and Network Auditor
Which of the following Windows processes supports creating and deleting processes and threads, running 16-bit virtual DOS machine processes, and running console windows?
You work as a Network Administrator for XYZ CORP. The company has a Linux-based network. You need to configure a firewall for the company. The firewall should be able to keep track of the state of network connections traveling across the network. Which of the following types of firewalls will you configure to accomplish the task?
Which of the following statements about session tracking is true?
Mark works as a project engineer in Tech Perfect Inc. His office is configured with Windows XP-based computers. The computer that he uses is not configured with a default gateway. He is able to access the Internet, but is not able to use e-mail services via the Internet. However, he is able to access e-mail services via the intranet of the company. Which of the following could be the reason of not being able to access e-mail services via the Internet?
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint. Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
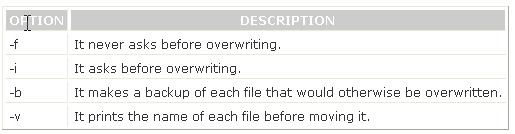
You have to move the whole directory /foo to /bar. Which of the following commands will you use to accomplish the task?
You have just installed a Windows 2003 server. What action should you take regarding the default shares?
Which of the following types of firewall functions at the Session layer of OSI model?
Which of the following wireless security features provides the best wireless security mechanism?



 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG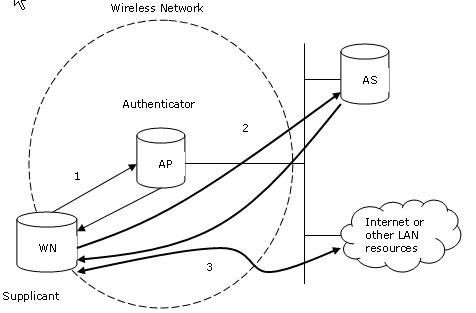 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG