Huawei H12-711_V4.0 - HCIA-Security V4.0 Exam
The keys used by the IPSec encryption and authentication algorithms can be configured manually or dynamically negotiated via the ____ protocol. (abbreviation, all uppercase).
Both digital envelopes and digital signatures guarantee data security and verify the origin of data.
When using passive mode to establish an FTP connection, the control channel uses port 20 and the data channel uses port 21. ( )[Multiple choice]*
Regarding the characteristics of the routing table, which of the following items is described correctly
The shard cache technology will wait for the arrival of the first shard packet, and then reassemble and decrypt all the packets, and then do subsequent processing by the device to ensure that the session can proceed normally in some application scenarios.
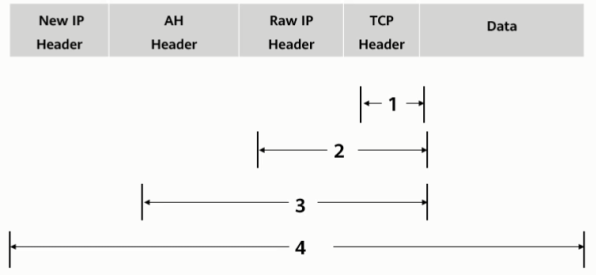
As shown in the figure, what is the authentication range of the AH protocol in tunnel mode?