Huawei H12-711_V4.0 - HCIA-Security V4.0 Exam
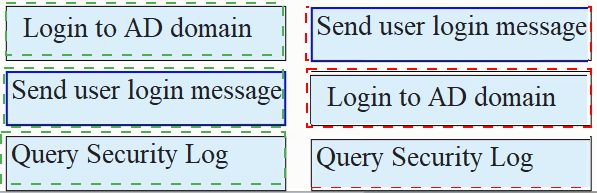
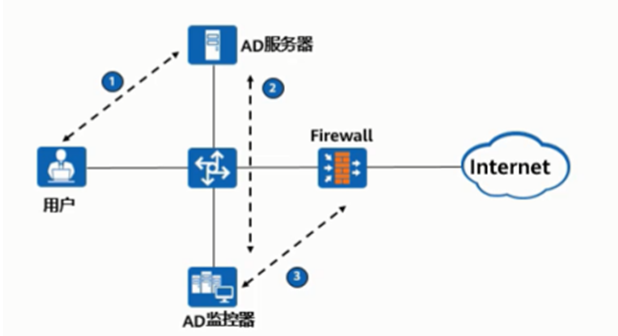
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.
____- The goal is to provide a rapid, composed and effective response in emergency situations, thereby enhancing the ability of the business to recover immediately from a disruptive event.[fill in the blank]*
Which of the following protocols is a multichannel protocol?
In cases where some configurations alter existing session table entries and want them to take effect immediately, you can regenerate the session table by clearing the session table information. All session table information can be cleared by executing the _____firewall session table command.
Which of the following is not included in the Business Impact Analysis (BIA).
Which of the following descriptions of server authentication is correct?
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
A Web server is deployed in an enterprise intranet to provide Web access services to Internet users, and in order to protect the access security of the server, it should be divided into the _____ area of the firewall.
What is the protocol number of the GRE protocol?
Digital envelope technology means that the sender uses the receiver's public key to encrypt the data, and then sends the ciphertext to the receiver ( )[Multiple choice]*