Huawei H12-721 - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
On an Eth-Trunk interface, traffic load balancing can be implemented by configuring different weights on member links.
In the firewall DDoS attack defense technology, the Anti-DDoS device adopts seven layers of defense technology, and the description based on session defense is correct?
The ACK flood attack is defended by the load check. The principle is that the cleaning device checks the payload of the ACK packet. If the payloads are all consistent (if the payload content is all 1), the packet is discarded.
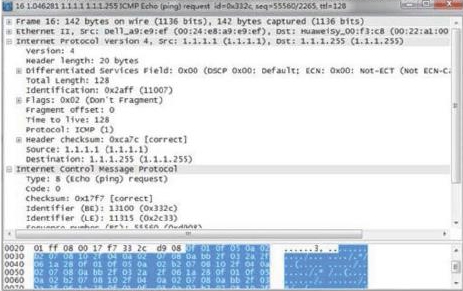
When an attack occurs, the result of packet capture on the attacked host (1.1.1.1) is as shown in the figure. What kind of attack is this attack?
IP address scanning attack defense not only prevents ICMP packet detection target addresses, but also prevents TCP/UDP scanning detection target addresses.
When using the optical bypass interface, the Bypass link has two working modes, automatic mode and forced mode.
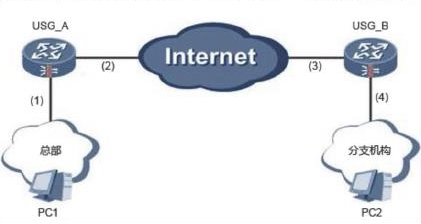
The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?
The first packet discarding technology of Huawei Anti-DDoS devices can defend against attack packets that continuously change the source IP address or source port number. The following is incorrect about the first packet discarding technology?
On the USG, you need to delete sslconfig.cfg in the hda1:/ directory. Which of the following commands can complete the operation?
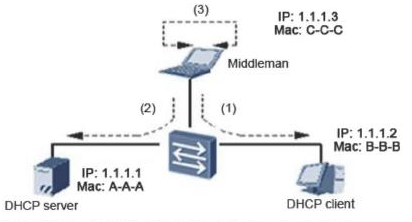
Man-in-the-middle attacks are: the middleman completes the data exchange between the server and the client. In the server's view, all messages are sent or sent to the client. From the client's point of view, all messages are also sent or sent.