Huawei H12-721 - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
Configure the remote packet capture function on the USG to download the device to the device. You can use the FTP server to analyze the packet.
Which of the following statements is correct about the IKE main mode and the aggressive mode?
What are the following attacks that are special message attacks?
71. Which option is incorrect about the HTTP Flood defense principle?
What are the correct statements about the following VRRP and VGMP protocol messages?
A certain network is as follows: LAN----G0/0/0 USG G0/0/1 ----Server. After the administrator analyzes the Attarcker on the LAN network connected to G0/0/0, if you want to prevent ARP flood attacks, limit the ARP traffic to 100 packets/minute. Which is the correct configuration?
IPSec VPN uses digital certificates for authentication. It has the following steps: 1. verify the certificate signature; 2. find the certificate serial number in the CRL; 3. share the entity certificate between the two devices; 4. verify the validity period of the certificate; . Establish a VPN tunnel. Which of the following is correct?
Which of the following is a disadvantage of L2TP VPN?
SSL VPN authentication is successful. Using the file sharing function, you can view directories and files, but you cannot upload, delete, and rename files. What are the possible reasons?
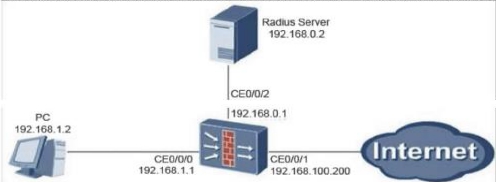
When using the Radius server to authenticate users, (the topology is as shown below), not only must the username and password be stored on the Radius server, but the username and password must also be configured on the firewall.