Huawei H12-721 - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
An attack source will spoof the server and send a large number of SYN-ACK packets to the attacking target network or server. If the destination port of the packet is the TCP service port of the attacked server, the TCP protocol stack of the server will be abnormal. What is it?
The ip-link principle is to continuously send ICMP packets or ARP request packets to the specified destination address, and check whether the ICMP echo reply or ARP reply packet of the destination IP response can be received.
What are the following attacks that are malformed?
A network is as follows: The l2tp vpn is established through the VPN Client and the USG (LNS). What are the reasons for the dialup failure?
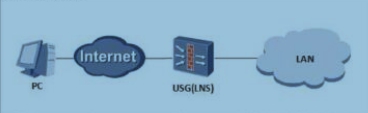
Which of the following statements is true about L2TP over IPSec VPN?
When configuring the USG hot standby, (assuming the backup group number is 1), the configuration command of the virtual address is correct?
In the USG firewall, which two commands can be used to view the running status and memory/CPU usage of the device components (main control board, board, fan, power supply, etc.)?
134. Which of the following is the connection status data to be backed up in the HRP function?
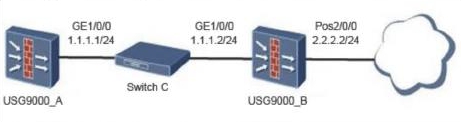
The topology of the BFD-bound static route is as follows: The administrator has configured the following on firewall A: [USG9000_A] bfd [USG9000_A-bfd] quit [USG9000_A] bfd aa bind peer-ip 1.1.1.2 [USG9000_A- Bfd session-aa] discriminator local 10 [USG9000_A-bfd session-aa] discriminator remote 20 Which of the following configurations can be added to the firewall to implement BFD-bound static routes?
In the DDoS attack defense, if the service learning function is used to find that there is no service or traffic of a certain service in normal traffic, you can use the blocking or traffic limiting method to defend against attacks on the Anti-DDoS device. .



