Huawei H12-721 - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
The ACK flood attack uses a botnet to send a large number of ACK packets, which impacts the network bandwidth and causes network link congestion. If the number of attack packets is large, the server processing performance is exhausted, thus rejecting normal services. Under the Huawei Anti-DDoS device to prevent this attack, compare the two processing methods - strict mode and basic mode, what is correct?
Which attack method is CC attack?
Virtual firewall technology can achieve overlapping IP addresses.
In the application scenario of IPSec traversal by NAT, the active initiator of the firewall must configure NAT traversal, and the firewall at the other end can be configured without NAT traversal.
Which of the following is correct about the configuration of the firewall interface bound to the VPN instance?
What are the three elements of an abnormal flow cleaning solution?
In the application scenario of the virtual firewall technology, the more common service is to provide rental services to the outside. If the virtual firewall VFW1 is leased to enterprise A and the virtual firewall VFW2 is leased to enterprise B, what is the following statement incorrect?
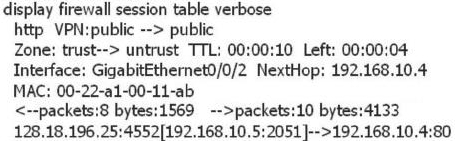
Based on the following information analysis on the firewall, which of the following options are correct?
DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
Which of the following security services can a secure multi-instance provide for a virtual firewall?



