Huawei H12-721 - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
A data flow has established a session in the firewall. If the packet filtering policy corresponding to the data is modified, how should the firewall execute?
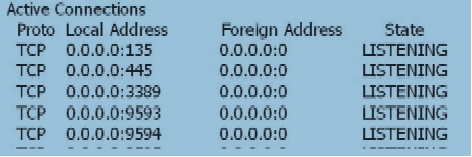
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
When the firewall works in the dual-system hot backup load balancing environment, if the upstream and downstream routers are working in the routing mode, you need to adjust the OSPF cost based on HRP.
A user wants to limit the maximum bandwidth of the 192.168.1.0/24 network segment to 500M, and limit all IP addresses in the network segment to maintain a bandwidth of 1M. How should I configure a current limiting policy for this requirement?
Networking as shown in the figure: PC1--USG--Router--PC2. If PC1 sends a packet to PC2, what are the three modes for the USG to process fragmented packets?
What are the correct descriptions of IPSec and IKE below?
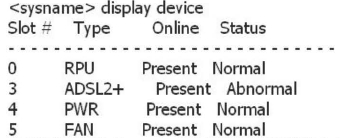
An administrator can view the status of the device components by the following command: The status of the Slot3 board is Abnormal. What are the possible causes of the following faults?
Which of the following statements about the blacklist is correct?
The following scan snoop attacks are:
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?



