Huawei H12-722 - Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0)
Single-packet attacks are divided into scanning and snooping attacks, malformed packet attacks, and special packet attacks. Ping of death is a special packet attack.
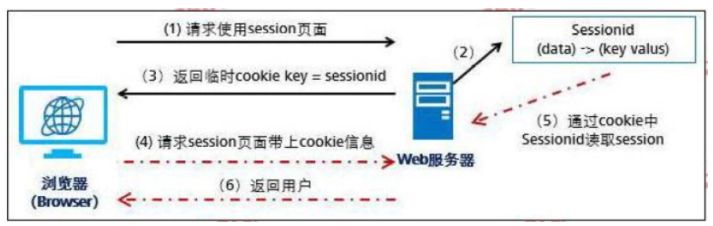
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
For the description of the principles of HTTP Flood and HTTPS Flood blow defense, which of the following options are correct? (multiple choice)



