Huawei H12-724 - HCIP-Security (Fast track) V1.0
Portal authentication on the Agile Controller-Campus has been configured and is correct.
Configure the following commands on the access control switch:
[S5720] authentication free-rule 1 destination ip 10.1.31.78 mask 255.255. 255.255
Which of the following options are correct? (multiple choice)
Visitors refer to users who need temporary access to the network at a specific location.
Jailbroken mobile terminal\Mobile terminals with non-compliant applications installed or terminals with non-compliant lock screen passwords connecting to the corporate network for office operations are not safe for companies. Any 0fice How to solve the problem of mobile office system?
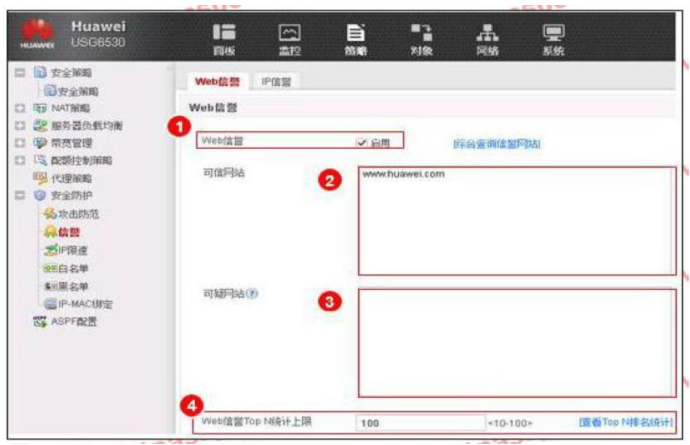
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
The following is the 802.1X access control switch configuration:
[S5720]dot1x authentication-method eap
[S5720-GigabitEthernet0/0/1] port link-type access
[S5720-GigabitEthemet0/0/1] port default vlan 11
[S5720-GigabitEthernet0/0/1] authentication dot1x
Assuming that GE0/0/1 is connected to user 1 and user 2 through the HUB, which of the following options is correct?
Which of the following options belong to the upgrade method of the anti-virus signature database of Huawei USG6000 products? (multiple choice)
For the URL is htpt://www.abcd. com:8080/news/education. aspx?name=tom &age=20, which option is path?
When using local guest account authentication, usually use(Portal The authentication method pushes the authentication page to the visitor. Before the user is authenticated, when the admission control device receives the HTTP The requested resource is not Portal Server authentication URL When, how to deal with the access control equipment.
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
The service free mobility function of the Agile Controller can guide the flow to the security center for processing according to the service, improving the utilization of physical equipment.



