Huawei H12-821_V1.0 - HCIP-Datacom-Core Technology V1.0
Which of the following statements regarding an IP prefix are true?
After which of the following parameters are modified does an IS-IS neighbor relationship need to re-established?
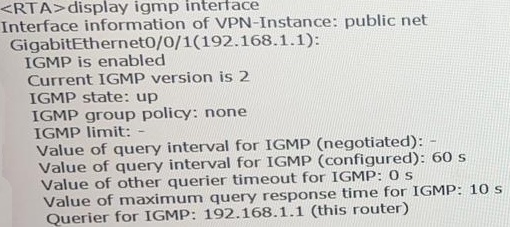
Which of the following statements is false, based on the following IGMP information on an interface of RTA?XC
In IPv6, interface IDs can be manually configured, automatically generated by the system, or generated based on the IEEE EUI-64 standard.
To inject IGP routes into BGP routes, you can only use the network command.
Which of the following attributes cannot be directly referenced in an apply clause of a route-policy?
L2TP does not provide security encryption. Therefore, other security measures, such as IPsec, are required to ensure the security of the entire tunnel for data transmission.
A large shopping mall configures a VLAN pool to prevent network performance deterioration caused by potentially large broadcast domains. A network engineer runs the display vlan pool name STA command to check information about the VLAN pool. The following command output is displayed:
Which of the following statements are true?
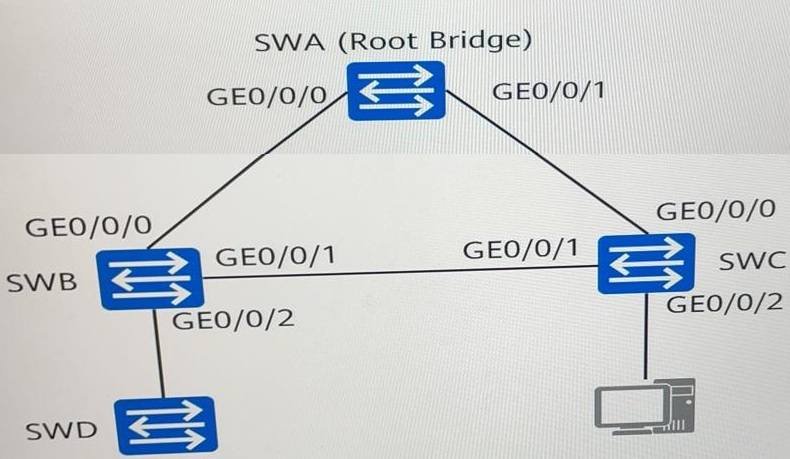
As shown in the figure, SWA, SWB, SWC, and SWD run the Rapid Spanning Tree Protocol (RSTP). Which of the following statements are true?
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?



