Huawei H12-891_V1.0 - HCIE-Datacom V1.0
Flavors are additional behaviors defined to enhance theEnd series instructionsinSRv6. Which of the followingEnd instructionscan thePSP flavorbe attached to?
Which of the following inter-AS MPLS L3VPN solutions needsASBRs to transmit VPNv4 routes?
Refer to the figure.
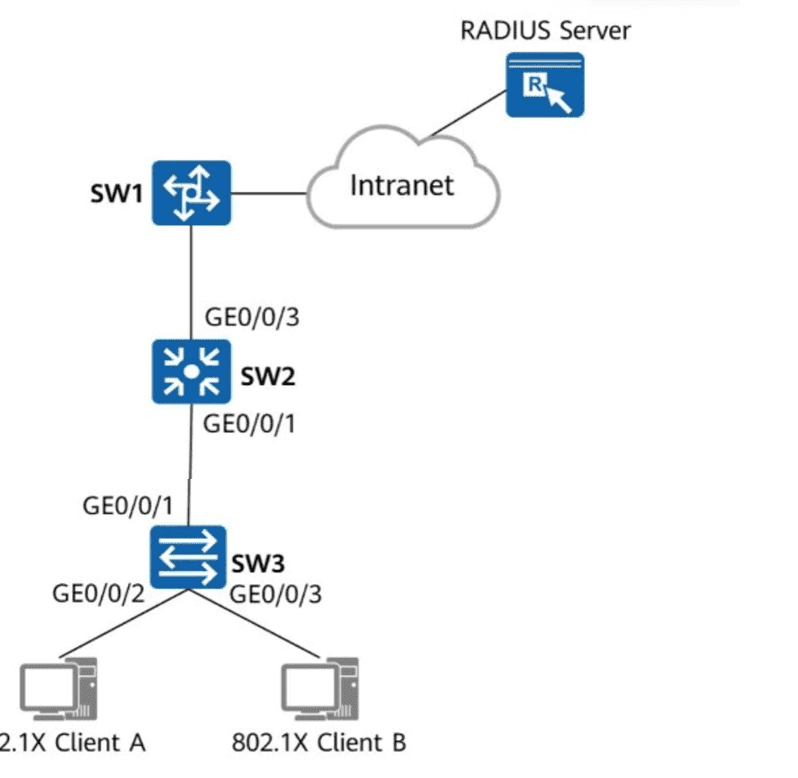
Which of the following steps are mandatory to enable 802.1X authentication on GE0/0/2 and GE0/0/3 of SW3 and configure a RADIUS server to authenticate and deliver network access rights to users?
Man-in-the-middle attacks (MITM) or IP/MAC Spoofing attacksare common onintranetsand can causeinformation leakage.
Which configuration method can prevent these attacks?
Huawei CloudCampus Solution has multiple application scenarios, and iMaster NCE-Campus provides different APIs for each application scenario. Match the following application scenarios with the open APIs provided by iMaster NCE-Campus.
Which of the following items are included in static information collection and analysis?



