HP HPE6-A68 - Aruba Certified ClearPass Professional (ACCP) 6.7
Refer to the exhibit.
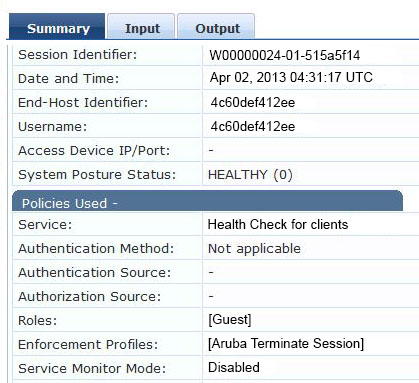
Based on the Access Tracker output for the user shown, which statement describes the status?
Refer to the exhibit.
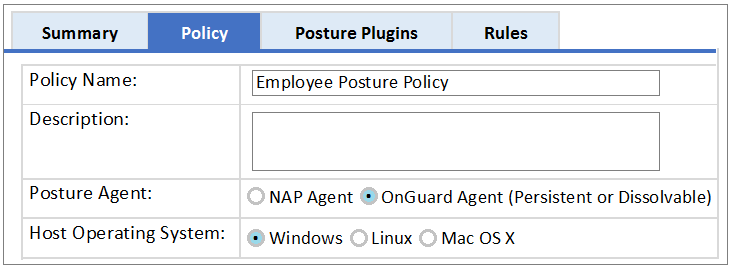
Based on the Posture Policy configuration shown, above, which statement is true?
When is the RADIUS server certificate used? (Select two.)
Refer to the exhibit.
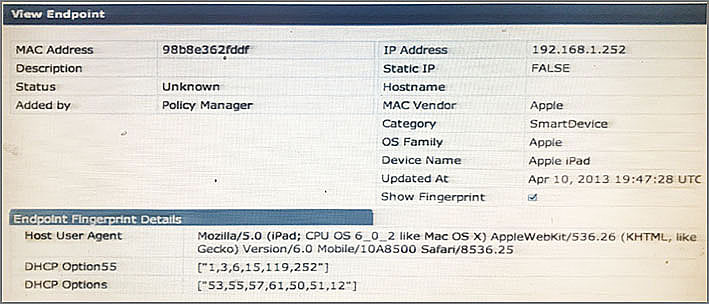
Based on the Endpoint information shown, which collectors were used to profile the device as Apple iPad? (Select two.)
Which devices support Apple over-the-air provisioning? (Select two.)
Refer to the exhibit.
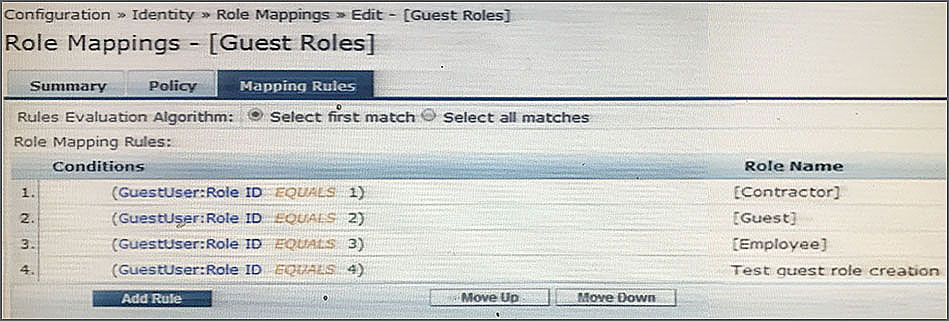
Based on the Guest Role Mapping Policy shown, what is the purpose of the Role Mapping Policy?
A hotel chain deployed ClearPass Guest. When hotel guests connect to the Guest SSID, launch a web browser and enter the address www.google.com, they are unable to immediately see the web login page.
What are the likely causes of this? (Select two.)
A guest self-registered through a Publisher’s Register page.
Which statement accurately describes how the guest’s account will be stored?
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server outage, 802.1x authentications will not be interrupted. The administrator has enabled a single Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
What are Operator Profiles used for?



