CrowdStrike IDP - CrowdStrike Certified Identity Specialist(CCIS) Exam
How does Identity Protection extend the capabilities of existing multi-factor authentication (MFA)?
For false positives, the Detection details can be set to new“Actionsâ€using:
Which of the following isNOTan available Goal within the Domain Security Overview?
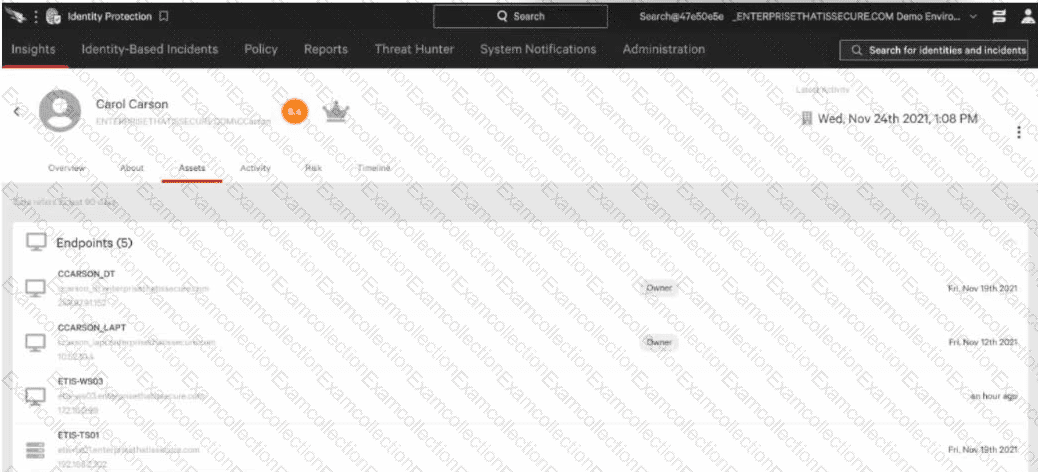
Which of the followingBESTindicates that this user has an established baseline?
How does CrowdStrike Falcon Identity Protection help customers identify different types of accounts in their domain?
Which of the following are minimum requirements for showing the Falcon Identity Verification Dialog on the end user’s machine?
What basic configuration fields are typically required for cloud Multi-Factor Authentication (MFA) connectors?
Which of the following statements isNOTtrue as it relates to Identity Events, Detections, and Incidents?
Which of the following MFA providers areNOTsupported by Falcon Identity?
Which menu option isNOTincluded in Falcon Identity Threat Detection (ITD)?



