PECB ISO-IEC-27001-Lead-Auditor - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Total 418 questions
Question
Which of the following is NOT a required element in the documentation template for quality review?
You received an email requiring you to send information such as name, email, and password in order to continue using your email account. If you do not send such
information, your email account will be disabled. What does this scenario present?
You are performing an ISO 27001 ISMS surveillance audit at a residential nursing home, ABC Healthcare Services. ABC uses a healthcare mobile app designed and maintained by a supplier, WeCare, to monitor residents' well-being. During the audit, you learn that 90% erf the residents' family members regularly receive medical device advertisements from WeCare, by email and SMS once a week. The service agreement between ABC and WeCare prohibits the supplier from using residents' personal data. ABC has received many complaints from residents and their family members.
The Service Manager says that the complaints were investigated as an information security incident which found that they were justified. Corrective actions have been planned and implemented according to the nonconformity and corrective action management procedure.
You write a nonconformity "ABC failed to comply with information security control A.5.34 (Privacy and protection of PII) relating to the personal data of residents' and their family members. A supplier, WeCare, used residents' personal information to send advertisements to family members"
Select three options of the corrections and corrective actions listed that you would expect ABC to make in response to the nonconformity
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security of the business continuity management process. During the audit, you learned that the organisation activated one of the business continuity plans (BCPs) to make sure the nursing service continued during the recent pandemic. You ask Service Manager to explain how the organisation manages information security during the business continuity management process.
The Service Manager presents the nursing service continuity plan for a pandemic and summarises the process as follows:
Stop the admission of any NEW residents.
70% of administration staff and 30% of medical staff will work from home.
Regular staff self-testing including submitting a negative test report 1 day BEFORE they come to the office.
Install ABC's healthcare mobile app, tracking their footprint and presenting a GREEN Health Status QR-Code for checking on the spot.
You ask the Service Manager how to prevent non-relevant family members or interested parties from accessing residents' personal data when staff work from home. The Service Manager cannot answer and suggests the n" Security Manager should help with that.
You would like to further investigate other areas to collect more audit evidence Select three options that will be in your audit trail.
Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life insurance. The company was founded in North Carolina, but have recently expanded in other locations, including Europe and Africa.
Sinvestment is committed to complying with laws and regulations applicable to their industry and preventing any information security incident. They have implemented an ISMS based on ISO/IEC 27001 and have applied for ISO/IEC 27001 certification.
Two auditors were assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment. they started the audit activities. First, they reviewed the documentation required by the standard, including the declaration of the ISMS scope, information security policies, and internal audits reports. The review process was not easy because, although Sinvestment stated that they had a documentation procedure in place, not all documents had the same format.
Then, the audit team conducted several interviews with Sinvestment's top management to understand their role in the ISMS implementation. All activities of the stage 1 audit were performed remotely, except the review of documented information, which took place on-site, as requested by Sinvestment.
During this stage, the auditors found out that there was no documentation related to information security training and awareness program. When asked, Sinvestment's representatives stated that the company has provided information security training sessions to all employees. Stage 1 audit gave the audit team a general understanding of Sinvestment's operations and ISMS.
The stage 2 audit was conducted three weeks after stage 1 audit. The audit team observed that the marketing department (which was not included in the audit scope) had no procedures in place to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the information security policy of the company, the issue was included in the audit report. In addition, during stage 2 audit, the audit team observed that Sinvestment did not record logs of user activities. The procedures of the company stated that "Logs recording user activities should be retained and regularly reviewed," yet the company did not present any evidence of the implementation of such procedure.
During all audit activities, the auditors used observation, interviews, documented information review, analysis, and technical verification to collect information and evidence. All the audit findings during stages 1 and 2 were analyzed and the audit team decided to issue a positive recommendation for certification.
During stage 1 audit, the audit team found out that Sinvestment did not have records on information security training and awareness. What Sinvestment do in this case? Refer to scenario 6.
Question
During an ISO/IEC 27001 certification audit, the audit team leader failed to follow established best practices for conducting the audit. In addition, they lacked the necessary expertise to assess some of the complex areas of the ISMS, leading to suboptimal results. While the audit findings were still reported, some areas of the audit are considered weak and the audit does not fully adhere to the required procedures.
Which level of responsibility does this scenario represent in the case of tortious acts?
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information security incident management procedure (Document reference ID: ISMS_L2_16, version 4).
You review the document and notice a statement "Any information security weakness, event, and incident should be reported to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences in the understanding of the meaning of the phrase "weakness, event, and incident".
The IT Security Manager explained that an online "information security handling" training seminar was conducted 6 months ago. All the people interviewed participated in and passed the reporting exercise and course assessment.
You would like to investigate other areas further to collect more audit evidence. Select three
options that would not be valid audit trails.
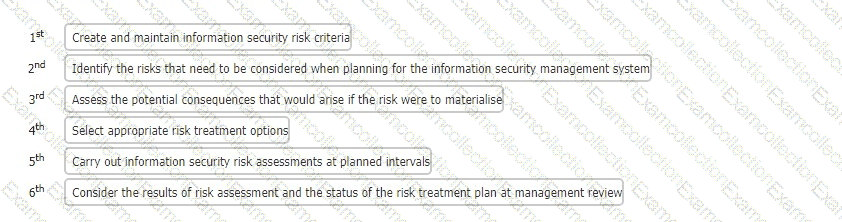
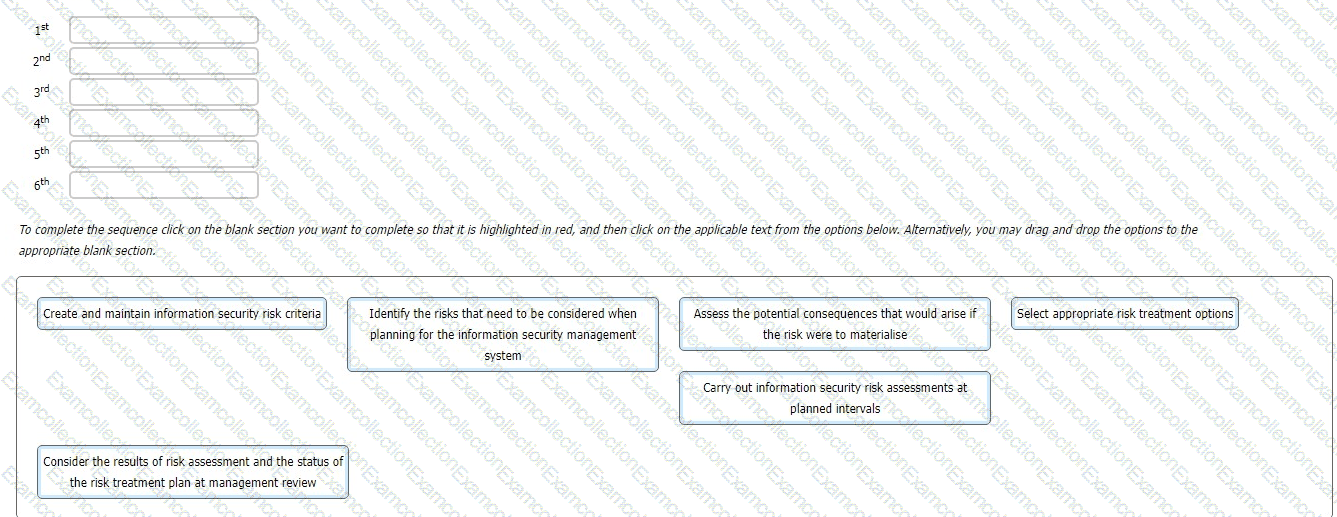
You are an experienced ISMS audit team leader providing instruction to a class of auditors in training. The subject of today's lesson is the management of information security risk in accordance with the requirements of ISO/IEC 27001:2022.
You provide the class with a series of activities. You then ask the class to sort these activities into the order in which they appear in the standard.
What is the correct sequence they should report back to you?
You are an experienced ISMS audit team leader providing guidance to an auditor in training. She asks you why it is important to have specific criteria relating to the grading of nonconformities.
Which one of the following responses is correct?
Because grading criteria provide a common basis for the evaluation of nonconformities across the organization
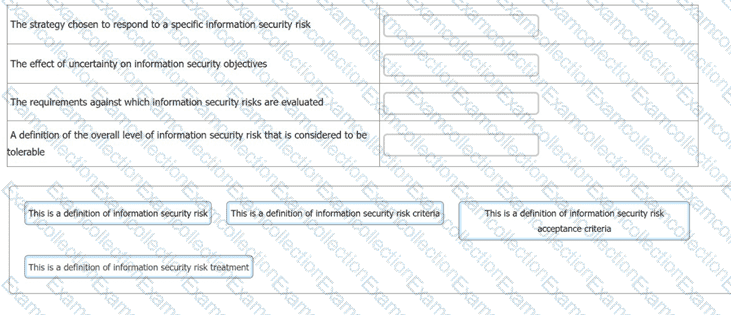
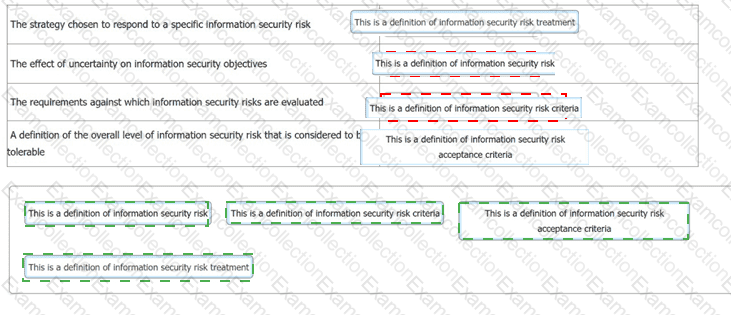
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company's risk management process.
He is attempting to update the current documentation to make it easier for other managers to understand, however, it is clear from your discussion he is confusing several key terms.
You ask him to match each of the descriptions with the appropriate risk term. What should the correct answers be?