PECB ISO-IEC-27001-Lead-Auditor - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Total 418 questions
Question:
Which of the following best defines managerial controls?
A data processing tool crashed when a user added more data in the buffer than its storage capacity allows. The incident was caused by the tool's inability to bound check arrays. What kind of vulnerability is this?
Scenario 6: Cyber ACrypt is a cybersecurity company that provides endpoint protection by offering anti-malware and device security, asset life cycle management, and device encryption. To validate its ISMS against ISO/IEC 27001 and demonstrate its commitment to cybersecurity excellence, the company underwent a meticulous audit process led by John, the appointed audit team leader.
Upon accepting the audit mandate, John promptly organized a meeting to outline the audit plan and team roles This phase was crucial for aligning the team with the audit's objectives and scope However, the initial presentation to Cyber ACrypt’s staff revealed a significant gap in understanding the audit's scope and objectives, indicating potential readiness challenges within the company
As the stage 1 audit commenced, the team prepared for on-site activities. They reviewed Cyber ACrypt's documented information, including the information security policy and operational procedures ensuring each piece conformed to and was standardized in format with author identification, production date, version number, and approval date Additionally, the audit team ensured that each document contained the information required by the respective clause of the standard This phase revealed that a detailed audit of the documentation describing task execution was unnecessary, streamlining the process and focusing the team's efforts on critical areas During the phase of conducting on-site activities, the team evaluated management responsibility for the Cyber Acrypt's policies This thorough examination aimed to ascertain continual improvement and adherence to ISMS requirements Subsequently, in the document, the stage 1 audit outputs phase, the audit team meticulously documented their findings, underscoring their conclusions regarding the fulfillment of the stage 1 objectives. This documentation was vital for the audit team and Cyber ACrypt to understand the preliminary audit outcomes and areas requiring attention.
The audit team also decided to conduct interviews with key interested parties. This decision was motivated by the objective of collecting robust audit evidence to validate the management system’s compliance with ISO/IEC 27001 requirements. Engaging with interested parties across various levels of Cyber ACrypt provided the audit team with invaluable perspectives and an understanding of the ISMS's implementation and effectiveness.
The stage 1 audit report unveiled critical areas of concern. The Statement of Applicability (SoA) and the ISMS policy were found to be lacking in several respects, including insufficient risk assessment, inadequate access controls, and lack of regular policy reviews. This prompted Cyber ACrypt to take immediate action to address these shortcomings. Their prompt response and modifications to the strategic documents reflected a strong commitment to achieving compliance.
The technical expertise introduced to bridge the audit team's cybersecurity knowledge gap played a pivotal role in identifying shortcomings in the risk assessment methodology and reviewing network architecture. This included evaluating firewalls, intrusion detection and prevention systems, and other network security measures, as well as assessing how Cyber ACrypt detects, responds to, and recovers from external and internal threats. Under John's supervision, the technical expert communicated the audit findings to the representatives of Cyber ACrypt. However, the audit team observed that the expert s objectivity might have been compromised due to receiving consultancy fees from the auditee. Considering the behavior of the technical expert during the audit, the audit team leader decided to discuss this concern with the certification body.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 6, was the objective of the interviews during the Stage 1 audit accordingly set by the audit team?
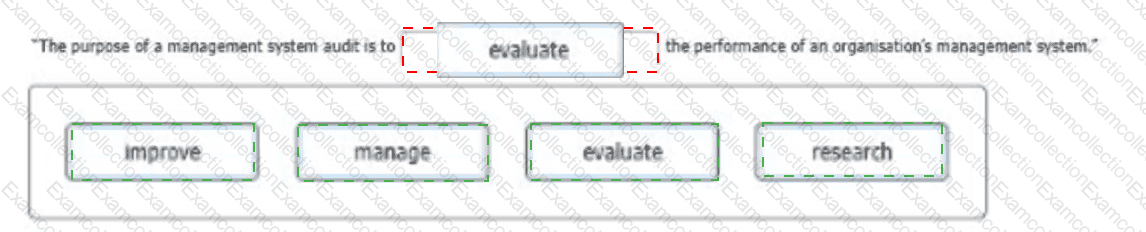
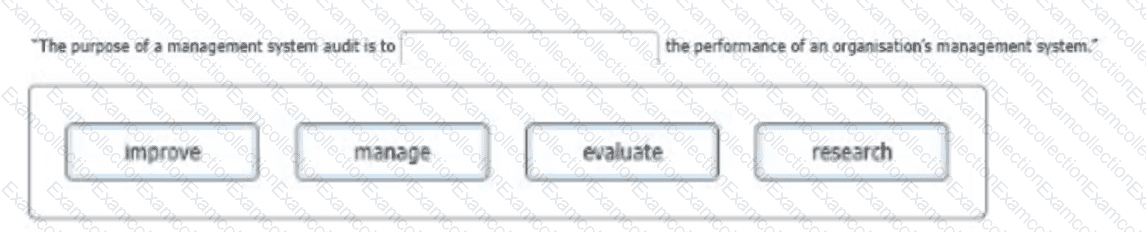
Select a word from the following options that best completes the sentence:
To complete the sentence with the word(s) click on the blank section you want to complete so that it is highlighted in red, and then click on the application text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
According to Scenario 6, was it appropriate for the audit team to include in the audit report the observed deficiency in the marketing department's access rights control procedures?
Scenario 1
Fintive is a distinguished security provider specializing in online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive offers services to companies operating online that seek to improve their information security, prevent fraud, and protect user information such as personally identifiable information (PII).
Fintive bases its decision-making and operational processes on previous cases, gathering customer data, classifying them according to the case, and analyzing them.
Initially, Fintive required a large number of employees to be able to conduct such complex analyses. However, as technology advanced, the company recognized an opportunity to implement a modern tool — a chatbot — to achieve pattern analyses aimed at preventing fraud in real time. This tool would also assist in improving customer service.
The initial idea was communicated to the software development team, who supported the initiative and were assigned to work on the project. They began integrating the chatbot into the existing system and set an objective regarding the chatbot, which was to answer 85% of all chat queries.
After successfully integrating the chatbot, the company released it for customer use. However, the chatbot exhibited several issues. Due to insufficient testing and a lack of sample data provided during the training phase — when it was supposed to learn the query pattern — the chatbot failed to effectively address user queries. Additionally, it sent random files to users when it encountered invalid inputs, such as unusual patterns of dots and special characters.
Consequently, the chatbot could not effectively answer customer queries, overwhelming traditional customer support and preventing them from assisting customers with their requests.
Recognizing the potential risks, Fintive decided to implement a set of new controls. The measures included enabling comprehensive audit logging, configuring automated alert systems to flag unusual activities, performing periodic access reviews, and monitoring system behavior for anomalies. The objective was to identify unauthorized access, errors, or suspicious activities in a timely manner, ensuring that any potential issues could be quickly recognized and investigated before causing significant harm.
Question
According to Scenario 1, which of the following could be a potential impact of the chatbot issues?
Which three of the following phrases are objectives' in relation to an audit?
Scenario:
Northstorm is an online retail shop offering unique vintage and modern accessories. It initially entered a small market but gradually grew thanks to the development of the overall e-commerce landscape. Northstorm works exclusively online and ensures efficient payment processing, inventory management, marketing tools, and shipment orders. It uses prioritized ordering to receive, restock, and ship its most popular products.
Northstorm has traditionally managed its IT operations by hosting its website and maintaining full control over its infrastructure, including hardware, software, and data administration. However, this approach hindered its growth due to the lack of responsive infrastructure. Seeking to enhance its e-commerce and payment systems, Northstorm opted to expand its in-house data centers, completing the expansion in two phases over three months. Initially, the company upgraded its core servers, point-of-sale, ordering, billing, database, and backup systems. The second phase involved improving mail, payment, and network functionalities. Additionally, during this phase, Northstorm adopted an international standard for personally identifiable information (PII) controllers and PII processors regarding PII processing to ensure its data handling practices were secure and compliant with global regulations.
Despite the expansion, Northstorm's upgraded data centers failed to meet its evolving business demands. This inadequacy led to several new challenges, including issues with order prioritization. Customers reported not receiving priority orders, and the company struggled with responsiveness. This was largely due to the main server's inability to process orders from YouDecide, an application designed to prioritize orders and simulate customer interactions. The application, reliant on advanced algorithms, was incompatible with the new operating system (OS) installed during the upgrade.
Faced with urgent compatibility issues, Northstorm quickly patched the application without proper validation, leading to the installation of a compromised version. This security lapse resulted in the main server being affected and the company's website going offline for a week. Recognizing the need for a more reliable solution, the company decided to outsource its website hosting to an e-commerce provider. The company signed a confidentiality agreement concerning product ownership and conducted a thorough review of user access rights to enhance security before transitioning.
Question:
Based on Scenario 1, which international standard did Northstorm adopt during the second phase of expansion?
In the context of a third-party certification audit, which two options state the management responsibilities of the audit team leader in managing the audit and the audit team?
Scenario:
Northstorm is an online retail shop offering unique vintage and modern accessories. It initially entered a small market but gradually grew thanks to the development of the overall e-commerce landscape. Northstorm works exclusively online and ensures efficient payment processing, inventory management, marketing tools, and shipment orders. It uses prioritized ordering to receive, restock, and ship its most popular products.
Northstorm has traditionally managed its IT operations by hosting its website and maintaining full control over its infrastructure, including hardware, software, and data administration. However, this approach hindered its growth due to the lack of responsive infrastructure. Seeking to enhance its e-commerce and payment systems, Northstorm opted to expand its in-house data centers, completing the expansion in two phases over three months. Initially, the company upgraded its core servers, point-of-sale, ordering, billing, database, and backup systems. The second phase involved improving mail, payment, and network functionalities. Additionally, during this phase, Northstorm adopted an international standard for personally identifiable information (PII) controllers and PII processors regarding PII processing to ensure its data handling practices were secure and compliant with global regulations.
Despite the expansion, Northstorm's upgraded data centers failed to meet its evolving business demands. This inadequacy led to several new challenges, including issues with order prioritization. Customers reported not receiving priority orders, and the company struggled with responsiveness. This was largely due to the main server's inability to process orders from YouDecide, an application designed to prioritize orders and simulate customer interactions. The application, reliant on advanced algorithms, was incompatible with the new operating system (OS) installed during the upgrade.
Faced with urgent compatibility issues, Northstorm quickly patched the application without proper validation, leading to the installation of a compromised version. This security lapse resulted in the main server being affected and the company's website going offline for a week. Recognizing the need for a more reliable solution, the company decided to outsource its website hosting to an e-commerce provider. The company signed a confidentiality agreement concerning product ownership and conducted a thorough review of user access rights to enhance security before transitioning.
Question:
Which of the following situations represents a vulnerability in Northstorm’s systems?