PECB ISO-IEC-27001-Lead-Auditor - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Question:
Which of the following statements regarding documented information in an organization's ISMS is incorrect?
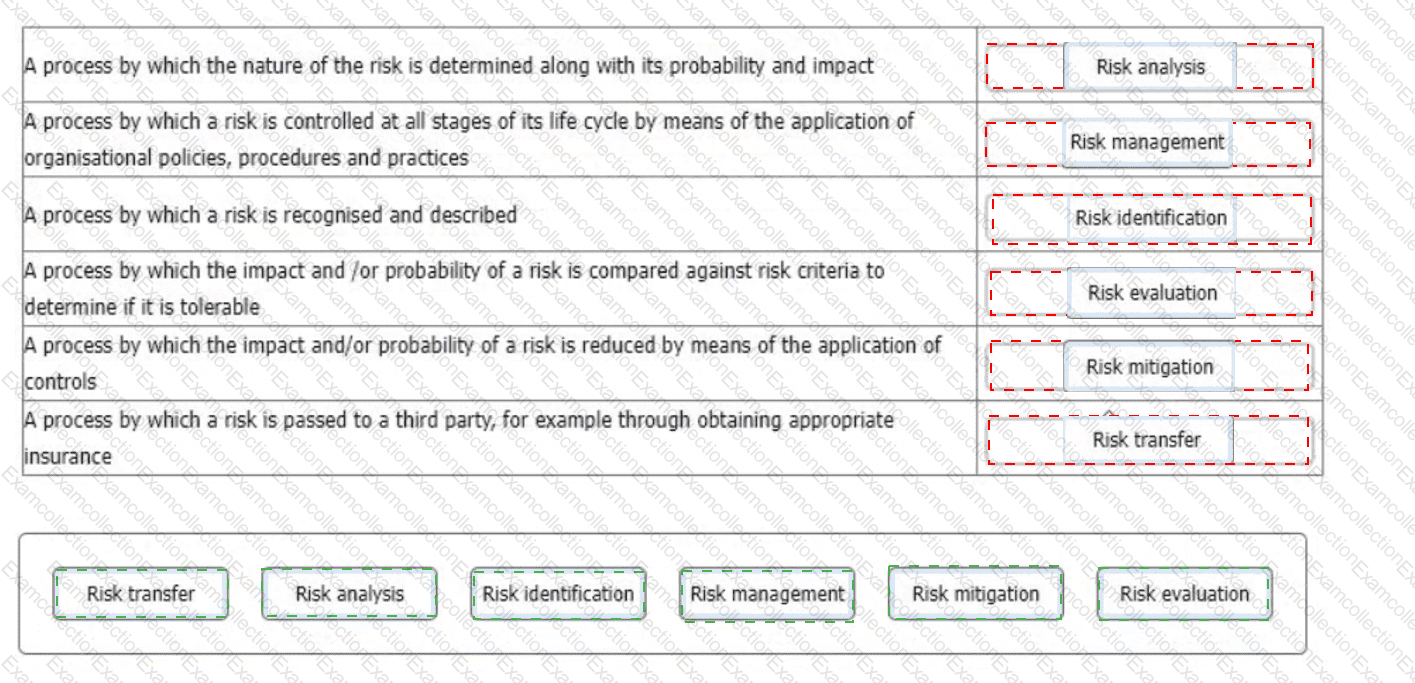
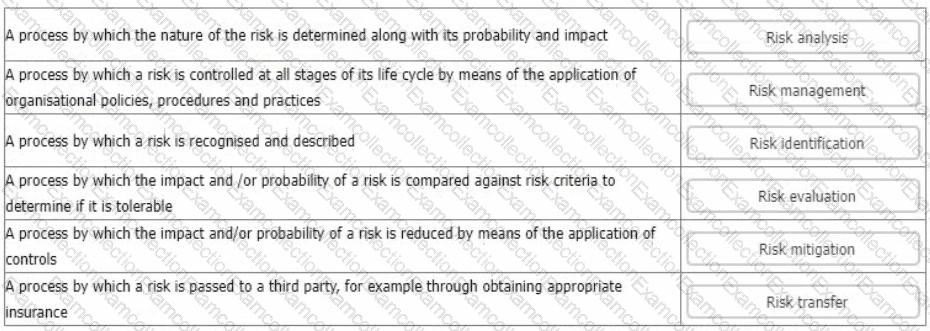
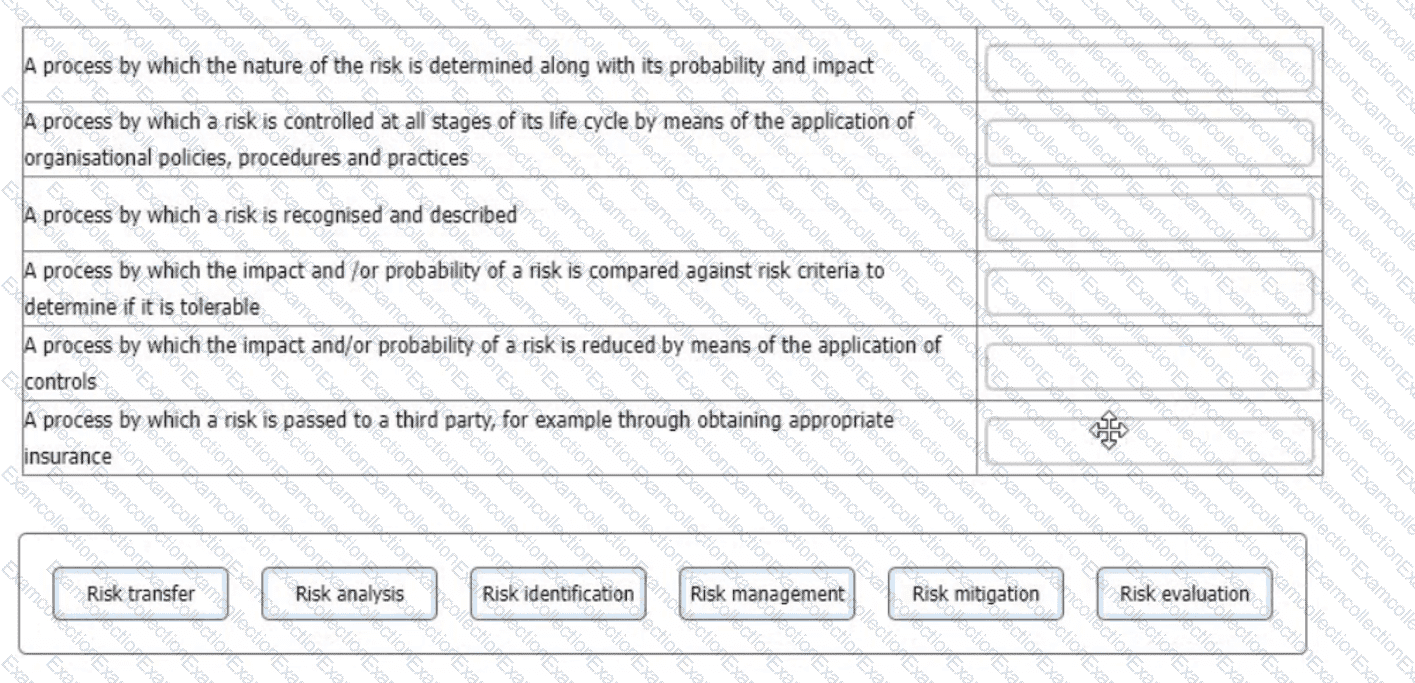
You are an experienced ISMS audit team leader providing instruction to an auditor in training. They are unclear in their understanding of risk processes and ask you to provide them with an example of each of the processes detailed below.
Match each of the descriptions provided to one of the following risk management processes.
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.
You are an experienced ISMS internal auditor.
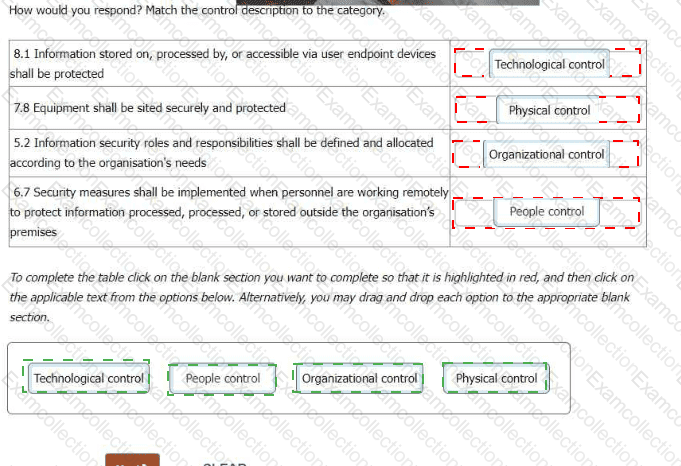
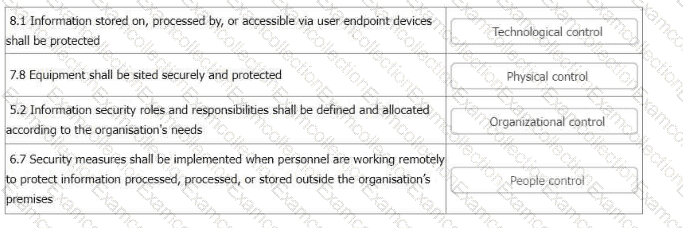
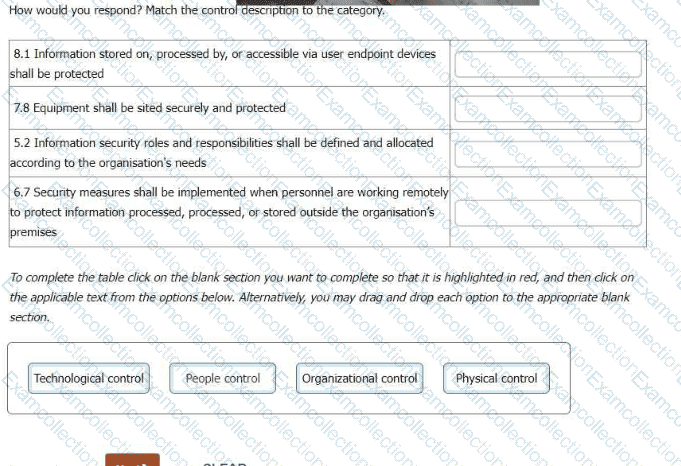
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company's Statement of Applicability.
The IT Manager is attempting to update the ISO/IEC 27001:2013 based Statement of Applicability to a Statement aligned to the 4 control themes present in ISO/IEC 27001:2022 (Organizational controls, People Controls, Physical Controls, Technical Controls).
The IT Manager is happy with their reassignment of controls, with the following exceptions. He asks you which of the four control categories each of the following should appear under.
AppFolk, a software development company, is seeking certification against ISO/IEC 27001. In the initial phases of the external audit, the certification body in discussion with the company excluded the marketing division from the audit scope, although they stated in their ISMS scope that the whole company is included. Is this acceptable?
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information
security incident management procedure (Document reference ID: ISMS_L2_16, version 4) and explains that the process is
based on ISO/IEC 27035-1:2016.
You review the document and notice a statement "any information security weakness, event, and incident should be reported
to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences
in the understanding of the meaning of "weakness, event, and incident".
The IT Security Manager explained that an online "information security handling" training seminar was conducted 6 months
ago. All of the interviewed persons participated in and passed the reporting exercise and course assessment.
You are preparing the audit findings. Select two options that are correct.
You ask the IT Manager why the organisation still uses the mobile app while personal data
encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymization functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That's why the Service Manager signed the approval.
You sample one of the medical staff's mobile and found that ABC's healthcare mobile app, version 1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app development company gave a free minor update on the tested software, performed an emergency release of the updated software, and gave a verbal guarantee that there will be no impact on any security functions. Based on his 20 years of information security experience, there is no need to re-test.
You are preparing the audit findings Select two options that are correct.
There is NO nonconformity (NC). The IT Manager demonstrates he is fully competent. (Relevant to clause 7.2)
In acceptable use of Information Assets, which is the best practice?
Question
An organization requires all employees to undergo security awareness training every six months. The training covers topics such as recognizing phishing attacks, handling sensitive data, and reporting security incidents. After completing the training, employees must pass a short quiz to demonstrate their understanding.
What type of control does this activity represent?
Which one option best describes the purpose of retaining documented information related to the Information Security Management System (ISMS) of an organisation?
Which one of the following options is the definition of the context of an organisation?