Juniper JN0-214 - Cloud Associate (JNCIA-Cloud)
You are asked to run a container in a Kubernetes environment.
What should you do to accomplish this task?
Create a JINJA2 template for the container and its resources.
Create a WYSYG definition for the container and its resources.
Define a YAML manifest for the container and its resources.
Define an XML configuration for the container and its resources.
The Answer Is:
CExplanation:
Kubernetes uses declarative configuration files to define and manage resources like containers, pods, and services. Let’s analyze each option:
A. Create a JINJA2 template for the container and its resources.
Incorrect:JINJA2 is a templating language often used in automation tools like Ansible. While it can generate Kubernetes manifests, Kubernetes itself does not use JINJA2 templates natively.
B. Create a WYSYG definition for the container and its resources.
Incorrect:"WYSYG" (What You See Is What You Get) is not a recognized format for Kubernetes configurations. Kubernetes relies on structured formats like YAML or JSON.
C. Define a YAML manifest for the container and its resources.
Correct:Kubernetes uses YAML (or JSON) manifests to define the desired state of resources, including containers, pods, and services. A YAML manifest specifies details like container images, resource limits, environment variables, and networking.
D. Define an XML configuration for the container and its resources.
Incorrect:Kubernetes does not use XML for defining resources. YAML is the standard format due to its readability and simplicity.
Why YAML Manifests?
Declarative Configuration:YAML manifests allow you to describe the desired state of your resources in a human-readable format.
Standard Practice:Kubernetes natively supports YAML for defining and deploying resources, making it the correct choice for this task.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes Kubernetes resource management, including YAML manifests. Understanding how to define and apply manifests is essential for deploying and managing containerized applications.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking features, relying on YAML manifests to configure resources.
Which OpenStack service displays server details of the compute node?
Keystone
Neutron
Cinder
Nova
The Answer Is:
DExplanation:
OpenStack provides various services to manage cloud infrastructure resources, including compute nodes and virtual machines (VMs). Let’s analyze each option:
A. Keystone
Incorrect: Keystoneis the OpenStack identity service responsible for authentication and authorization. It does not display server details of compute nodes.
B. Neutron
Incorrect: Neutronis the OpenStack networking service that manages virtual networks, routers, and IP addresses. It is unrelated to displaying server details of compute nodes.
C. Cinder
Incorrect: Cinderis the OpenStack block storage service that provides persistent storage volumes for VMs. It does not display server details of compute nodes.
D. Nova
Correct: Novais the OpenStack compute service responsible for managing the lifecycle of virtual machines, including provisioning, scheduling, and monitoring. It also provides detailed information about compute nodes and VMs, such as CPU, memory, and disk usage.
Why Nova?
Compute Node Management:Nova manages compute nodes and provides APIs to retrieve server details, including resource utilization and VM status.
Integration with CLI/REST APIs:Commands likeopenstack server showornova hypervisor-showcan be used to display compute node and VM details.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack services, including Nova, as part of its cloud infrastructure curriculum. Understanding Nova’s role in managing compute resources is essential for operating OpenStack environments.
For example, Juniper Contrail integrates with OpenStack Nova to provide advanced networking and security features for compute nodes and VMs.
Theopenstack user listcommand uses which OpenStack service?
Cinder
Keystone
Nova
Neutron
The Answer Is:
BExplanation:
OpenStack provides various services to manage cloud infrastructure resources, including user management. Let’s analyze each option:
A. Cinder
Incorrect: Cinderis the OpenStack block storage service that provides persistent storage volumes for virtual machines. It is unrelated to managing users.
B. Keystone
Correct: Keystoneis the OpenStack identity service responsible for authentication, authorization, and user management. Theopenstack user listcommand interacts with Keystone to retrieve a list of users in the OpenStack environment.
C. Nova
Incorrect: Novais the OpenStack compute service that manages virtual machine instances. It does not handle user management.
D. Neutron
Incorrect: Neutronis the OpenStack networking service that manages virtual networks, routers, and IP addresses. It is unrelated to user management.
Why Keystone?
Identity Management:Keystone serves as the central identity provider for OpenStack, managing users, roles, and projects.
API Integration:Commands likeopenstack user listrely on Keystone's APIs to query and display user information.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack services, including Keystone, as part of its cloud infrastructure curriculum. Understanding Keystone’s role in user management is essential for operating OpenStack environments.
For example, Juniper Contrail integrates with OpenStack Keystone to enforce authentication and authorization for network resources.
Click the Exhibit button.
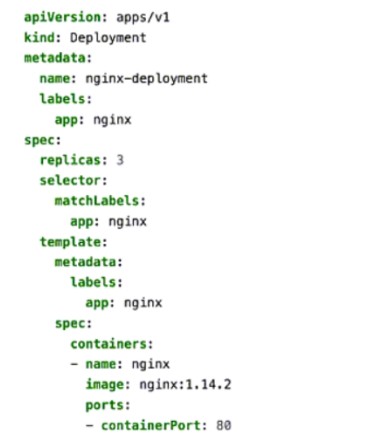
You apply the manifest file shown in the exhibit.
Which two statements are correct in this scenario? (Choose two.)
The created pods are receiving traffic on port 80.
This manifest is used to create a deployment.
This manifest is used to create a deploymentConfig.
Four pods are created as a result of applying this manifest.
The Answer Is:
A, BExplanation:
The provided YAML manifest defines a Kubernetes Deployment object that creates and manages a set of pods running the NGINX web server. Let’s analyze each statement in detail:
A. The created pods are receiving traffic on port 80.
Correct:
The containerPort: 80 field in the manifest specifies that the NGINX container listens on port 80 for incoming traffic.
While this does not expose the pods externally, it ensures that the application inside the pod (NGINX) is configured to receive traffic on port 80.
B. This manifest is used to create a deployment.
Correct:
The kind: Deployment field explicitly indicates that this manifest is used to create a Kubernetes Deployment .
Deployments are used to manage the desired state of pods, including scaling, rolling updates, and self-healing.
C. This manifest is used to create a deploymentConfig.
Incorrect:
deploymentConfig is a concept specific to OpenShift, not standard Kubernetes. In OpenShift, deploymentConfig provides additional features like triggers and lifecycle hooks, but this manifest uses the standard Kubernetes Deployment object.
D. Four pods are created as a result of applying this manifest.
Incorrect:
The replicas: 3 field in the manifest specifies that the Deployment will create three replicas of the NGINX pod. Therefore, only three pods are created, not four.
Why These Statements?
Traffic on Port 80:
The containerPort: 80 field ensures that the NGINX application inside the pod listens on port 80. This is critical for the application to function as a web server.
Deployment Object:
The kind: Deployment field confirms that this manifest creates a Kubernetes Deployment, which manages the lifecycle of the pods.
Replica Count:
The replicas: 3 field explicitly states that three pods will be created. Any assumption of four pods is incorrect.
Additional Context:
Kubernetes Deployments:Deployments are one of the most common Kubernetes objects used to manage stateless applications. They ensure that the desired number of pod replicas is always running and can handle updates or rollbacks seamlessly.
Ports in Kubernetes:The containerPort field in the pod specification defines the port on which thecontainerized application listens. However, to expose the pods externally, a Kubernetes Service (e.g., NodePort, LoadBalancer) must be created.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes concepts, including Deployments, Pods, and networking. Understanding how Deployments work and how ports are configured is essential for managing containerized applications in cloud environments.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking and security features for Deployments like the one described in the exhibit.
You want to create a template that defines the CPU, RAM, and disk space properties that a VM will use when instantiated.
In this scenario, which OpenStack object should you create?
role
Image
project
flavor
The Answer Is:
DExplanation:
In OpenStack, aflavordefines the compute, memory, and storage properties of a virtual machine (VM) instance. Let’s analyze each option:
A. role
Incorrect:Aroledefines permissions and access levels for users within a project. It is unrelated to defining VM properties.
B. Image
Incorrect:Animageis a template used to create VM instances. While images define the operating system and initial configuration, they do not specify CPU, RAM, or disk space properties.
C. project
Incorrect:Aproject(or tenant) represents an isolated environment for managing resources. It does not define the properties of individual VMs.
D. flavor
Correct:Aflavorspecifies the CPU, RAM, and disk space properties that a VM will use when instantiated. For example, a flavor might define a VM with 2 vCPUs, 4 GB of RAM, and 20 GB of disk space.
Why Flavor?
Resource Specification:Flavors allow administrators to define standardized resource templates for VMs, ensuring consistency and simplifying resource allocation.
Flexibility:Users can select the appropriate flavor based on their workload requirements, making it easy to deploy VMs with predefined configurations.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack concepts, including flavors, as part of its cloud infrastructure curriculum. Understanding how flavors define VM properties is essential for managing compute resources effectively.
For example, Juniper Contrail integrates with OpenStack Nova to provide advanced networking features for VMs deployed using specific flavors.
What are two available installation methods for an OpenShift cluster? (Choose two.)
installer-provisioned infrastructure
kubeadm
user-provisioned infrastructure
kubespray
The Answer Is:
A, CExplanation:
OpenShift provides multiple methods for installing and deploying clusters, depending on the level of control and automation desired. Let’s analyze each option:
A. installer-provisioned infrastructure
Correct:
Installer-provisioned infrastructure (IPI)is an automated installation method where the OpenShift installer provisions and configures the underlying infrastructure (e.g., virtual machines, networking) using cloud provider APIs or bare-metal platforms. This method simplifies deployment by handling most of the setup automatically.
B. kubeadm
Incorrect:
kubeadmis a tool used to bootstrap Kubernetes clusters manually. While it is widely used for Kubernetes installations, it is not specific to OpenShift and is not an official installation method for OpenShift clusters.
C. user-provisioned infrastructure
Correct:
User-provisioned infrastructure (UPI)is a manual installation method where users prepare and configure the infrastructure (e.g., virtual machines, load balancers, DNS) before deploying OpenShift. This method provides greater flexibility and control over the environment but requires more effort from the user.
D. kubespray
Incorrect:
Kubesprayis an open-source tool used to deploy Kubernetes clusters on various infrastructures. Likekubeadm, it is not specific to OpenShift and is not an official installation method for OpenShift clusters.
Why These Methods?
Installer-Provisioned Infrastructure (IPI):Automates the entire installation process, making it ideal for users who want a quick and hassle-free deployment.
User-Provisioned Infrastructure (UPI):Allows advanced users to customize the infrastructure and tailor the deployment to their specific needs.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenShift installation methods as part of its curriculum on container orchestration platforms. Understanding the differences between IPI and UPI is essential for deploying OpenShift clusters effectively.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, regardless of whether the cluster is deployed using IPI or UPI.
Which type of virtualization provides containerization and uses a microservices architecture?
hardware-assisted virtualization
OS-level virtualization
full virtualization
paravirtualization
The Answer Is:
BExplanation:
Virtualization technologies enable the creation of isolated environments for running applications or services. Let’s analyze each option:
A. hardware-assisted virtualization
Incorrect: Hardware-assisted virtualization (e.g., Intel VT-x, AMD-V) provides support for running full virtual machines (VMs) on physical hardware. It is not related to containerization or microservices architecture.
B. OS-level virtualization
Correct: OS-level virtualization enables containerization , where multiple isolated user-space instances (containers) run on a single operating system kernel. Containers are lightweight and share the host OS kernel, making them ideal for microservices architectures. Examples include Docker and Kubernetes.
C. full virtualization
Incorrect: Full virtualization involves running a complete guest operating system on top of a hypervisor (e.g., VMware ESXi, KVM). While it provides strong isolation, it is not as lightweight or efficient as containerization for microservices.
D. paravirtualization
Incorrect: Paravirtualization involves modifying the guest operating system to communicate directly with the hypervisor. Like full virtualization, it is used for running VMs, not containers.
Why OS-Level Virtualization?
Containerization: OS-level virtualization creates isolated environments (containers) that share the host OS kernel but have their own file systems, libraries, and configurations.
Microservices Architecture: Containers are well-suited for deploying microservices because they are lightweight, portable, and scalable.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding virtualization technologies, including OS-level virtualization. Containerization is a key component of modern cloud-native architectures, enabling efficient deployment of microservices.
For example, Juniper Contrail integrates with Kubernetes to manage containerized workloads in cloud environments. OS-level virtualization is fundamental to this integration.
Which two statements describe a multitenant cloud? (Choose two.)
Tenants are aware of other tenants using their shared resources.
Servers, network, and storage are separated per tenant.
The entities of each tenant are isolated from one another.
Multiple customers of a cloud vendor have access to their own dedicated hardware.
The Answer Is:
C, DExplanation:
Amultitenant cloudis a cloud architecture where multiple customers (tenants) share the same physical infrastructure or platform while maintaining logical isolation. Let’s analyze each statement:
A. Tenants are aware of other tenants using their shared resources.
Incorrect:In a multitenant cloud, tenants are logically isolated from one another. While they may share underlying physical resources (e.g., servers, storage), they are unaware of other tenants and cannot access their data or applications. This isolation ensures security and privacy.
B. Servers, network, and storage are separated per tenant.
Incorrect:In a multitenant cloud, resources such as servers, network, and storage are shared among tenants. The separation is logical, not physical. For example, virtualization technologies like hypervisors and software-defined networking (SDN) are used to create isolated environments for each tenant.
C. The entities of each tenant are isolated from one another.
Correct:Logical isolation is a fundamental characteristic of multitenancy. Each tenant’s data, applications, and configurations are isolated to prevent unauthorized access or interference. Technologies like virtual private clouds (VPCs) and network segmentation ensure this isolation.
D. Multiple customers of a cloud vendor have access to their own dedicated hardware.
Correct:While multitenancy typically involves shared resources, some cloud vendors offer dedicated hardware options for customers with strict compliance or performance requirements. For example, AWS offers "Dedicated Instances" or "Dedicated Hosts," which provide dedicated physical servers for specific tenants within a multitenant environment.
JNCIA Cloud References:
The Juniper Networks Certified Associate - Cloud (JNCIA-Cloud) curriculum discusses multitenancy as a key feature of cloud computing. Multitenancy enables efficient resource utilization and cost savings by allowing multiple tenants to share infrastructure while maintaining isolation.
For example, Juniper Contrail supports multitenancy by providing features like VPCs, network overlays, and tenant isolation. These capabilities ensure that each tenant has a secure and independent environment within a shared infrastructure.
Which two statements are correct about the Kubernetes networking model? (Choose two.)
Pods are allowed to communicate if they are only in the default namespaces.
Pods are not allowed to communicate if they are in different namespaces.
Full communication between pods is allowed across nodes without requiring NAT.
Each pod has its own IP address in a flat, shared networking namespace.
The Answer Is:
C, DExplanation:
Kubernetes networking is designed to provide seamless communication between pods, regardless of their location in the cluster. Let’s analyze each statement:
A. Pods are allowed to communicate if they are only in the default namespaces.
Incorrect:Pods can communicate with each other regardless of the namespace they belong to. Namespaces are used for logical grouping and isolation but do not restrict inter-pod communication.
B. Pods are not allowed to communicate if they are in different namespaces.
Incorrect:Pods in different namespaces can communicate with each other as long as there are no network policies restricting such communication. Namespaces do not inherently block communication.
C. Full communication between pods is allowed across nodes without requiring NAT.
Correct:Kubernetes networking is designed so that pods can communicate directly with each other across nodes without Network Address Translation (NAT). Each pod has a unique IP address, and the underlying network ensures direct communication.
D. Each pod has its own IP address in a flat, shared networking namespace.
Correct:In Kubernetes, each pod is assigned a unique IP address in a flat network space. This allows pods to communicate with each other as if they were on the same network, regardless of the node they are running on.
Why These Statements?
Flat Networking Model:Kubernetes uses a flat networking model where each pod gets its own IP address, simplifying communication and eliminating the need for NAT.
Cross-Node Communication:The design ensures that pods can communicate seamlessly across nodes, enabling scalable and distributed applications.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes Kubernetes networking concepts, including pod-to-pod communication and the flat networking model. Understanding these principles is essential for designing and managing Kubernetes clusters.
For example, Juniper Contrail provides advanced networking features for Kubernetes, ensuring efficient and secure pod communication across nodes.
Which OpenStack object enables multitenancy?
role
flavor
image
project
The Answer Is:
DExplanation:
Multitenancy is a key feature of OpenStack, enabling multiple users or organizations to share cloud resources while maintaining isolation. Let’s analyze each option:
A. role
Incorrect:Aroledefines permissions and access levels for users within a project. While roles are important for managing user privileges, they do not directly enable multitenancy.
B. flavor
Incorrect:Aflavorspecifies the compute, memory, and storage capacity of a VM instance. It is unrelated to enabling multitenancy.
C. image
Incorrect:Animageis a template used to create VM instances. While images are essential for deploying VMs, they do not enable multitenancy.
D. project
Correct:Aproject(also known as a tenant) is the primary mechanism for enabling multitenancy in OpenStack. Each project represents an isolated environment where resources (e.g., VMs, networks, storage) are provisioned and managed independently.
Why Project?
Isolation:Projects ensure that resources allocated to one tenant are isolated from others, enabling secure and efficient resource sharing.
Resource Management:Each project has its own quotas, users, and resources, making it the foundation of multitenancy in OpenStack.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding OpenStack’s multitenancy model, including the role of projects. Recognizing how projects enable resource isolation is essential for managing shared cloud environments.
For example, Juniper Contrail integrates with OpenStack Keystone to enforce multitenancy and network segmentation for projects.



