Juniper JN0-335 - Security, Specialist (JNCIS-SEC)
Which two statements are correct about the cSRX? (Choose two.)
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two statements about SRX Series device chassis clusters are true? (Choose two.)
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
You want to show tabular data for operational mode commands.
In this scenario, which logging parameter will provide this function?
Exhibit
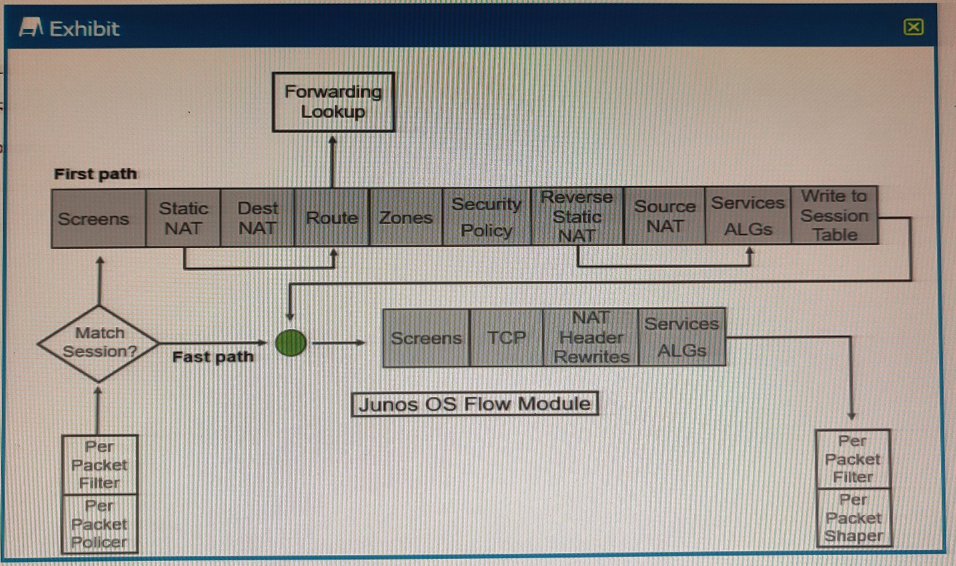
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Your JIMS server is unable to view event logs.
Which two actions would you take to solve this issue? (Choose two.)



