Juniper JN0-335 - Security, Specialist (JNCIS-SEC)
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
What are two requirements for enabling AppQoE? (Choose two.)
Exhibit
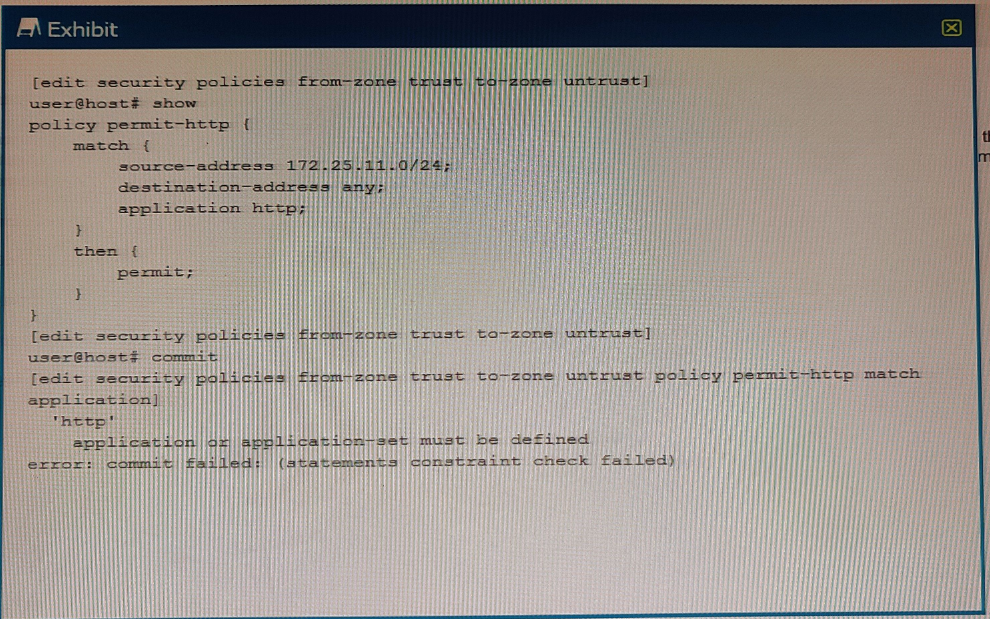
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
Regarding static attack object groups, which two statements are true? (Choose two.)
Exhibit
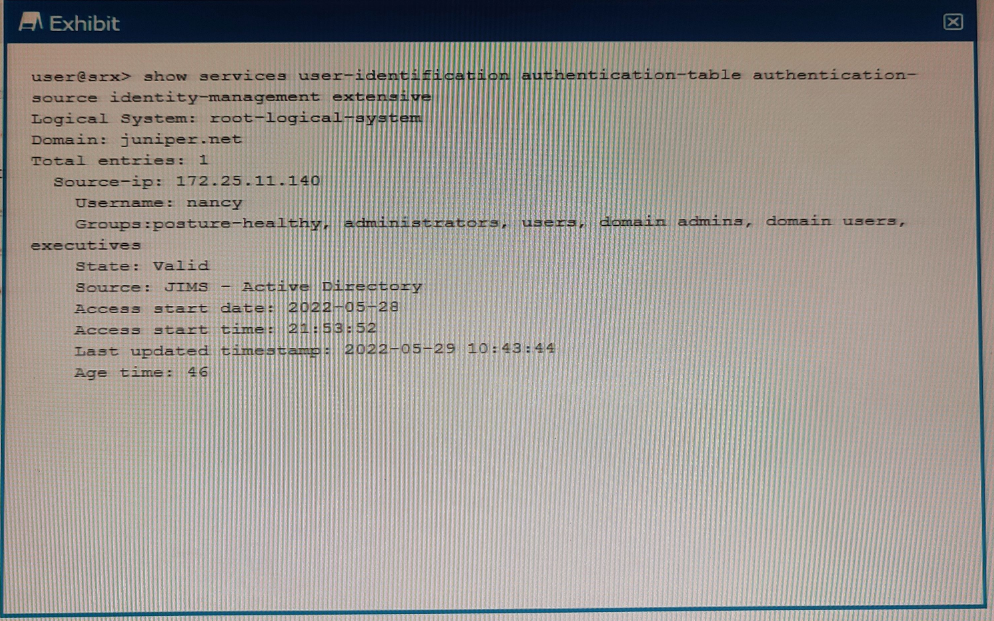
Referring to the exhibit, which two statements are true? (Choose two.)
Which statement regarding Juniper Identity Management Service (JIMS) domain PC probes is true?
Exhibit
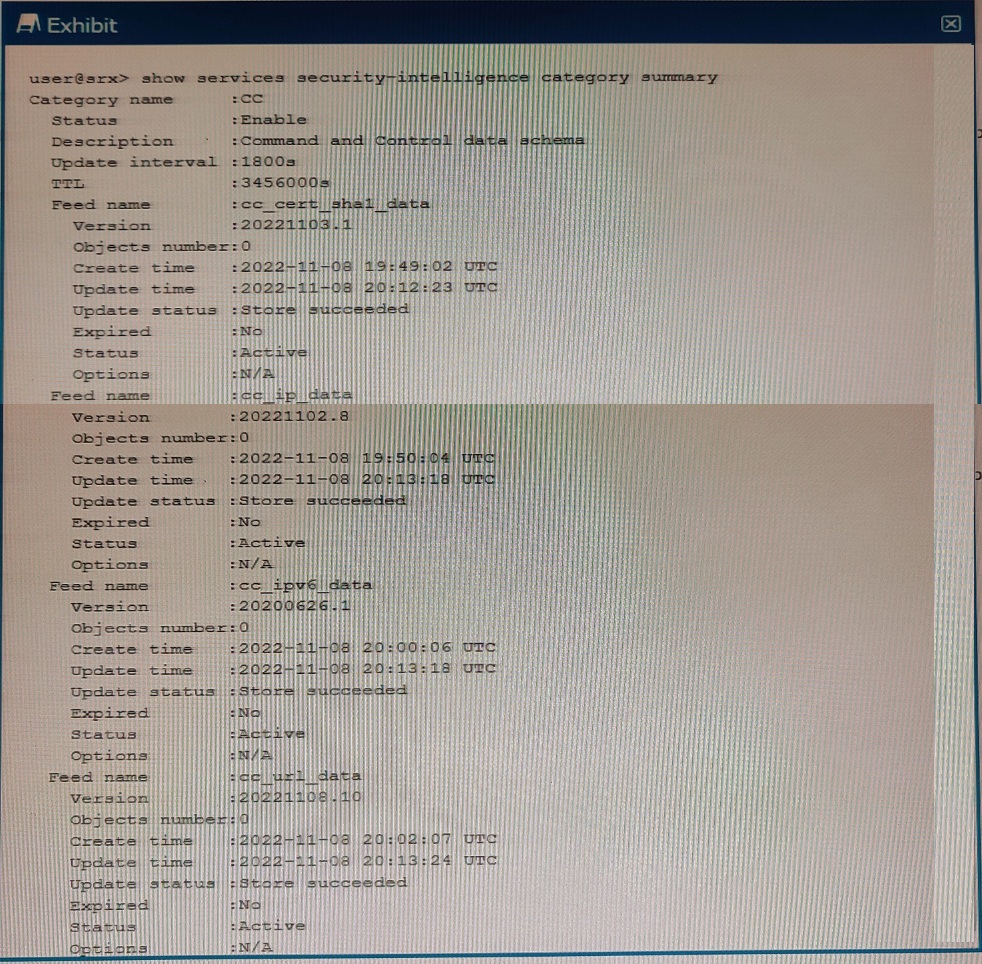
You just finished setting up your command-and-control (C&C) category with Juniper ATP Cloud. You notice that all of the feeds have zero objects in them.
Which statement is correct in this scenario?
On which three Hypervisors is vSRX supported? (Choose three.)
You have implemented a vSRX in your VMware environment. You want to implement a second vSRX Series device and enable chassis clustering.
Which two statements are correct in this scenario about the control-link settings? (Choose two.)



