Juniper JN0-636 - Security, Professional (JNCIP-SEC)
You are asked to look at a configuration that is designed to take all traffic with a specific source ip address and forward the
traffic to a traffic analysis server for further evaluation. The configuration is no longer working as intended.
Referring to the exhibit which change must be made to correct the configuration?
Exhibit.
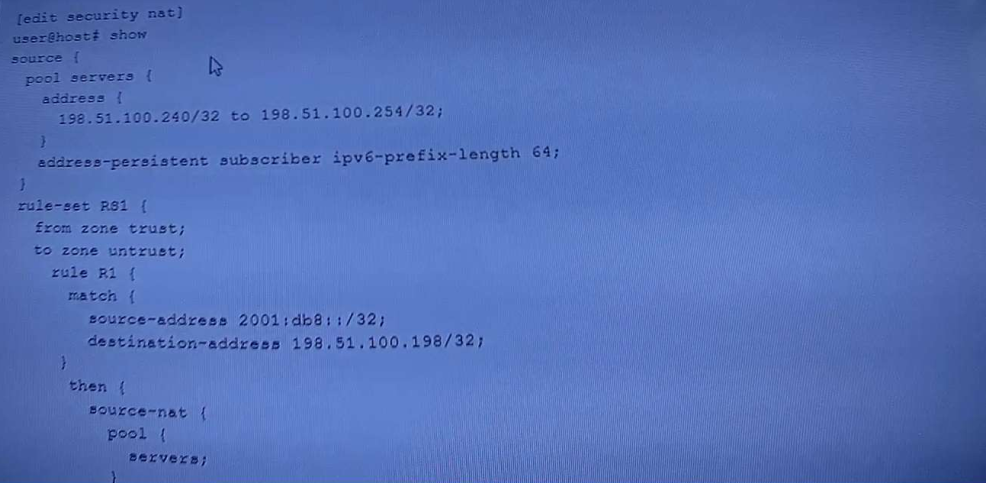
Referring to the exhibit, which two statements are true? (Choose two.)
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
Exhibit
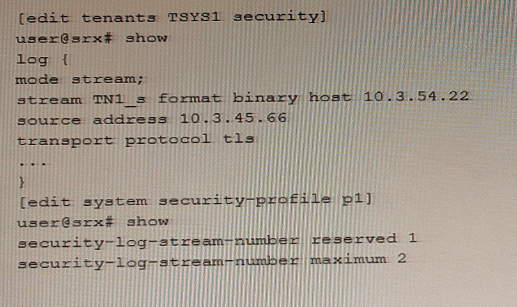
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
You are requested to enroll an SRX Series device with Juniper ATP Cloud.
Which statement is correct in this scenario?
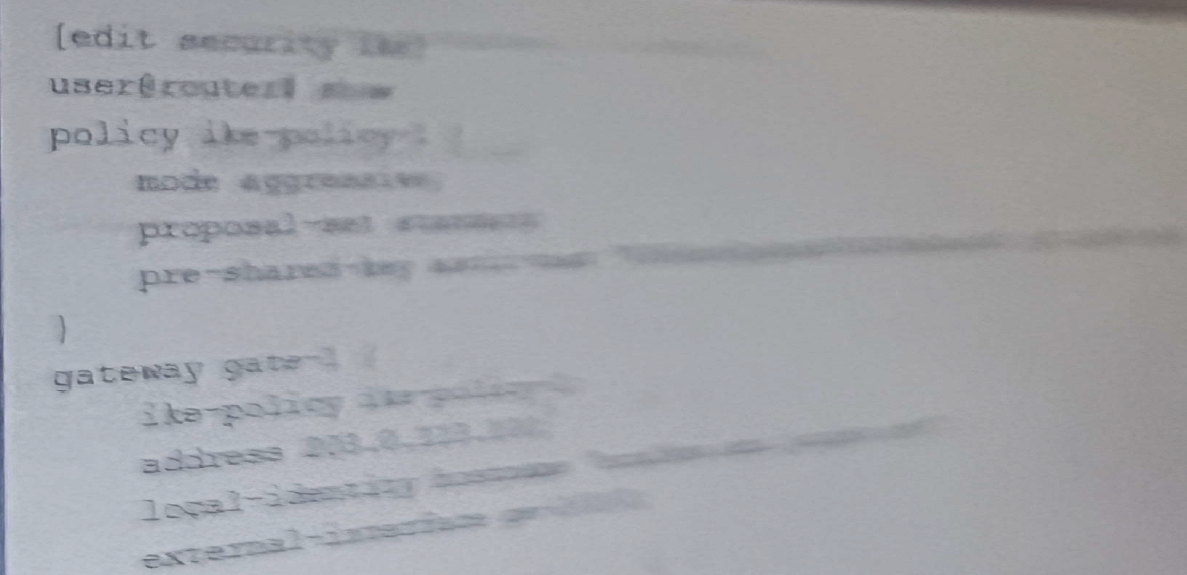
which two statements about the configuration shown in the exhibit are correct ?
Exhibit:
Exhibit
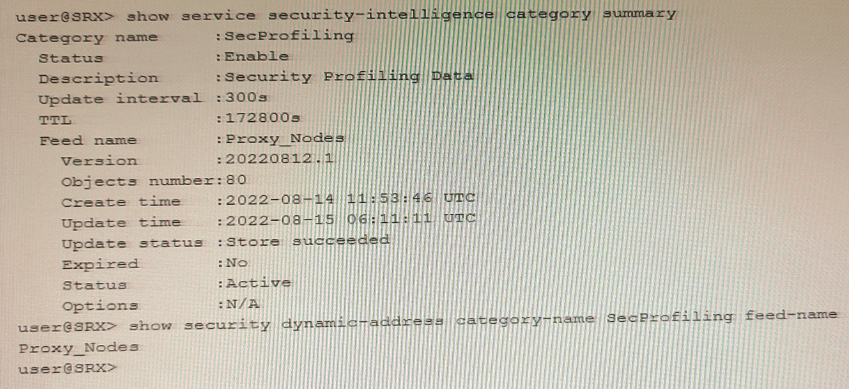
You have recently configured Adaptive Threat Profiling and notice 20 IP address entries in the monitoring section of the Juniper ATP Cloud portal that do not match the number of entries locally on the SRX Series device, as shown in the exhibit.
What is the correct action to solve this problem on the SRX device?
Which two types of source NAT translations are supported in this scenario? (Choose two.)
Exhibit
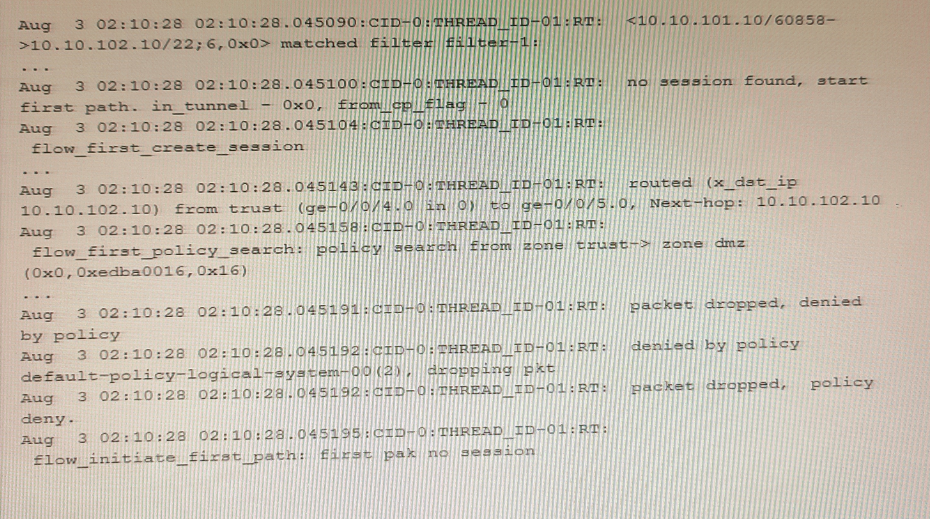
Which two statements are correct about the output shown in the exhibit? (Choose two.)
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)



