Juniper JN0-636 - Security, Professional (JNCIP-SEC)
Exhibit
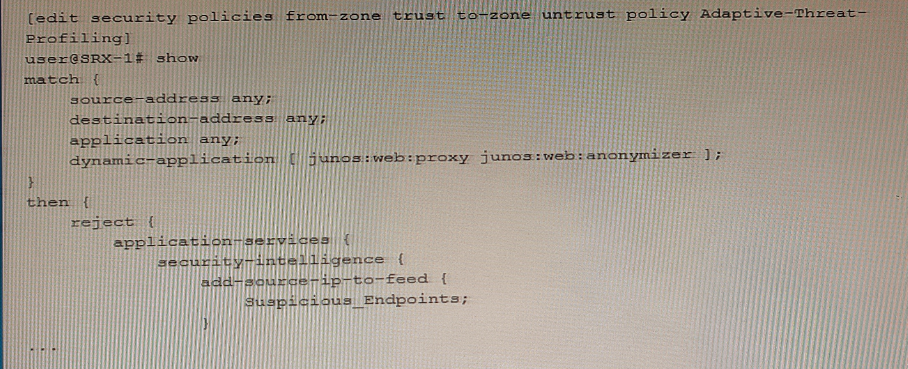
Referring to the exhibit, which two statements are true? (Choose two.)
you must find an infected host and where the a􀆩ack came from using the Juniper ATP Cloud. Which two monitor workspaces will return the requested information? (Choose Two)
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
Exhibit:
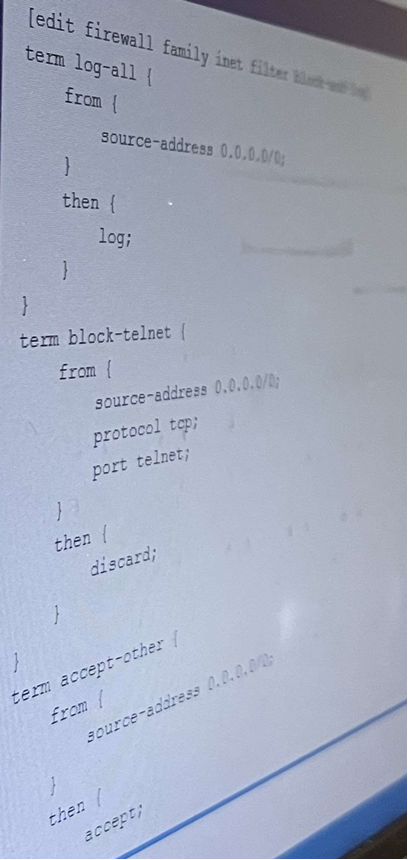
You are troubleshooting a firewall filter shown in the exhibit that is intended to log all traffic and block
only inbound telnet traffic on interface ge-0/0/3.
How should you modify the configuration to fulfill the requirements?
All interfaces involved in transparent mode are configured with which protocol family?
You are connecting two remote sites to your corporate headquarters site. You must ensure that all traffic is secured and sent directly between sites In this scenario, which VPN should be used?
You are asked to control access to network resources based on the identity of an authenticated device
Which three steps will accomplish this goal on the SRX Series firewalls? (Choose three )
Exhibit

You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
You are connecting two remote sites to your corporate headquarters site; you must ensure that all traffic is secured and
only uses a single Phase 2 SA for both sites.
In this scenario, which VPN should be used?
Exhibit
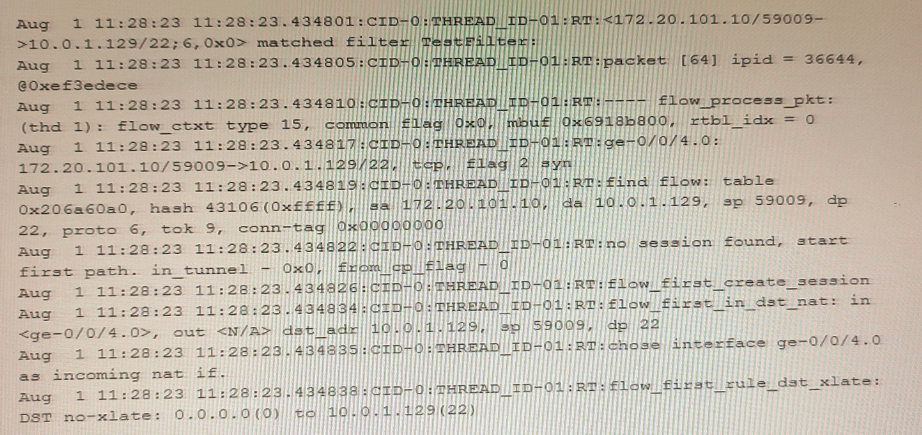
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)



