Juniper JN0-636 - Security, Professional (JNCIP-SEC)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
your company wants to take your juniper ATP appliance into private mode. You must give them a list
of impacted features for this request.
Which two features are impacted in this scenario? (Choose two)
Exhibit:
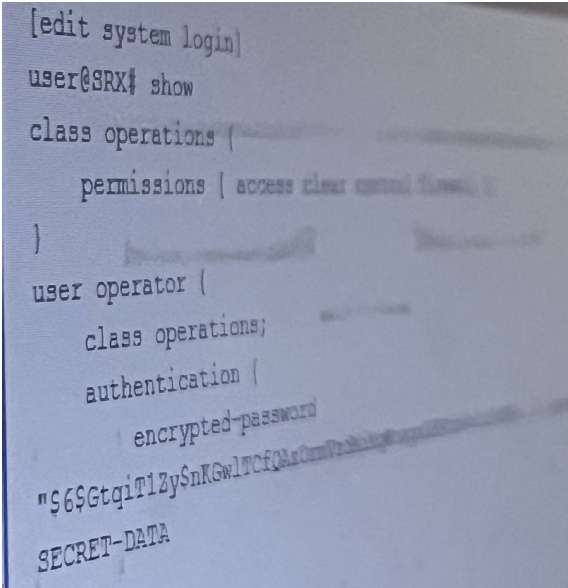
Referring to the exhibit, the operator user is unable to save configuration files to a usb stick the is
plugged into SRX. What should you do to solve this problem?
What is the purpose of the Switch Microservice of Policy Enforcer?
You want to identify potential threats within SSL-encrypted sessions without requiring SSL proxy to decrypt the session contents. Which security feature achieves this objective?
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
Exhibit
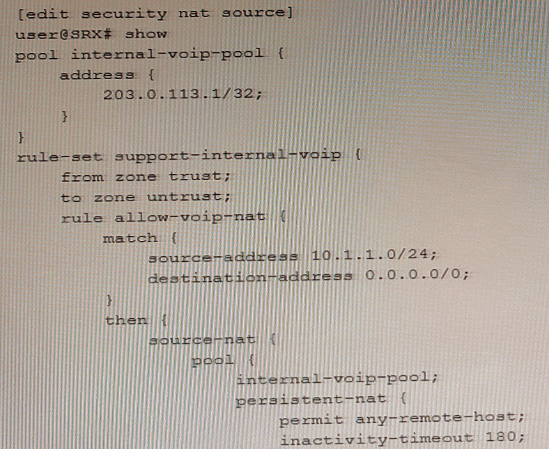
Referring to the exhibit, an internal host is sending traffic to an Internet host using the 203.0.113.1 reflexive address with source port 54311.
Which statement is correct in this situation?
Exhibit
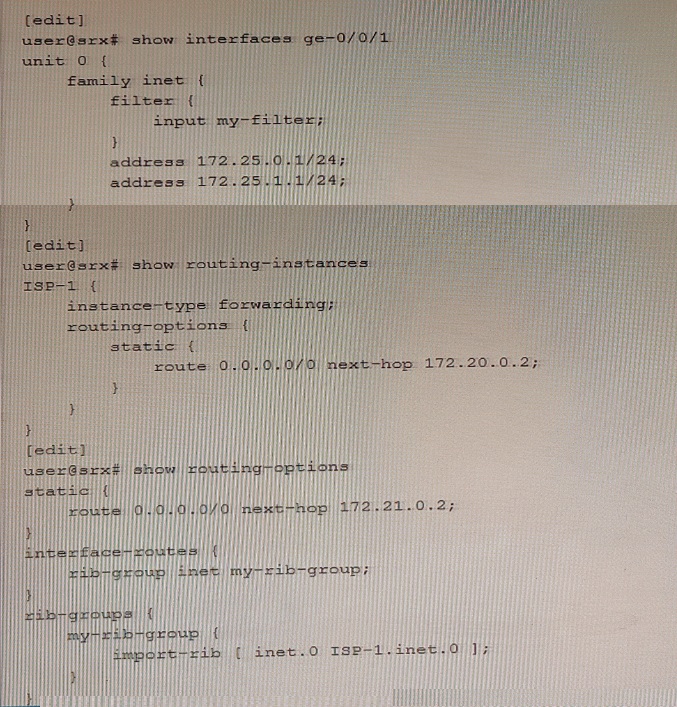
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?



