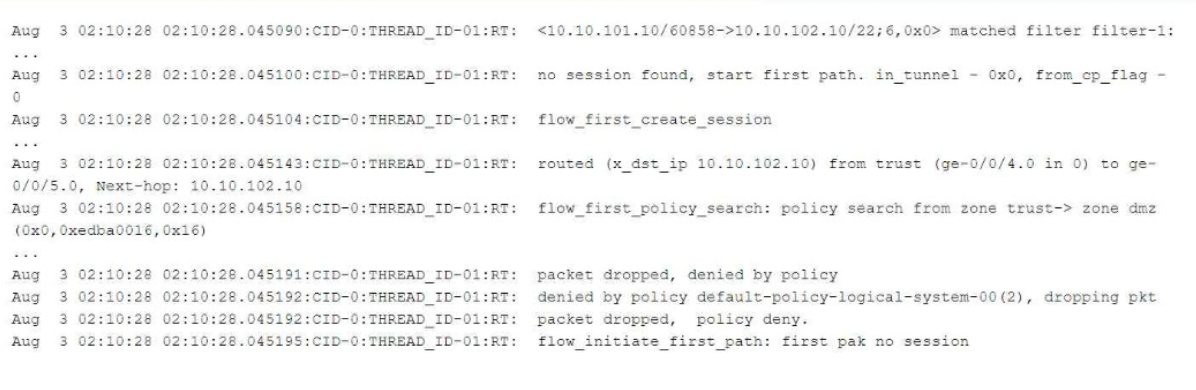
From the flow logs in the exhibit, we can observe the following key events:
The session creation was initiated (flow_first_create_session), but the policy search failed (flow_first_policy_search), which implies that no matching policy was found between the zones involved (zone trust-> zone dmz).
The packet was dropped with the reason "denied by policy." This shows that the packet was dropped either due to no matching security policy or because the default policy denies the traffic (packet dropped, denied by policy).
The line denied by policy default-policy-logical-system-00(2) indicates that the default security policy is responsible for denying the traffic, confirming that no explicit security policy was configured to allow this traffic.
Explanation of Answer A (Dropped by the default security policy):
The log message clearly states that the packet was dropped by the default security policy (default-policy-logical-system-00). In Junos, when a session is attempted between two zones and no explicit policy exists to allow the traffic, the default policy is to deny the traffic. This is a common behavior in Junos OS when a security policy does not explicitly allow traffic between zones.
The information displayed in the log involves session creation, flow policy search, and packet dropping due to policy violations, which are all part of basic packet processing in the data path. This type of information is logged when the traceoptions flag is set to basic-datapath. The basic-datapath traceoption provides detailed information about the forwarding process, including policy lookups and packet drops, which is precisely what we see in the exhibit.
The traceoptions flag host-traffic (Answer C) is incorrect because host-traffic is typically used for traffic destined to or generated from the Junos device itself (e.g., SSH or SNMP traffic to the SRX device), not for traffic passing through the device.
To capture flow processing details like those shown, you need the basic-datapath traceoptions flag, which provides details about packet forwarding and policy evaluation.
Step-by-Step Configuration for Tracing (Basic-Datapath):
To capture detailed information about how traffic is being processed, including policy lookups and flow session creation, enable traceoptions for the flow.
bash
set security flow traceoptions file flow-log
set security flow traceoptions flag basic-datapath
bash
commit
Once enabled, you can check the trace logs for packet flows, policy lookups, and session creation details:
bash
show log flow-log
This log will contain information similar to the exhibit, including session creation attempts and packet drops due to security policy.
Juniper Security Reference:
Default Security Policies: Juniper SRX devices have a default security policy to deny all traffic that is not explicitly allowed by user-defined policies. This is essential for security best practices. Reference: Juniper Networks Documentation on Security Policies.
Traceoptions for Debugging Flows: Using traceoptions is crucial for debugging and understanding how traffic is handled by the SRX, particularly when issues arise from policy misconfigurations or routing. Reference: Juniper Traceoptions.
By using the basic-datapath traceoptions, you can gain insights into how the device processes traffic, including policy lookups, route lookups, and packet drops, as demonstrated in the exhibit.
==========