Juniper JN0-649 - Enterprise Routing and Switching Professional (JNCIP-ENT)
A user is attempting to watch a high-definition video being streamed from the media server over the network. However, the user complains that the experienced video quality is poor. While logged on to router B, a Juniper Networks device, you notice that video packets are being dropped.
In this scenario, what would solve this problem?
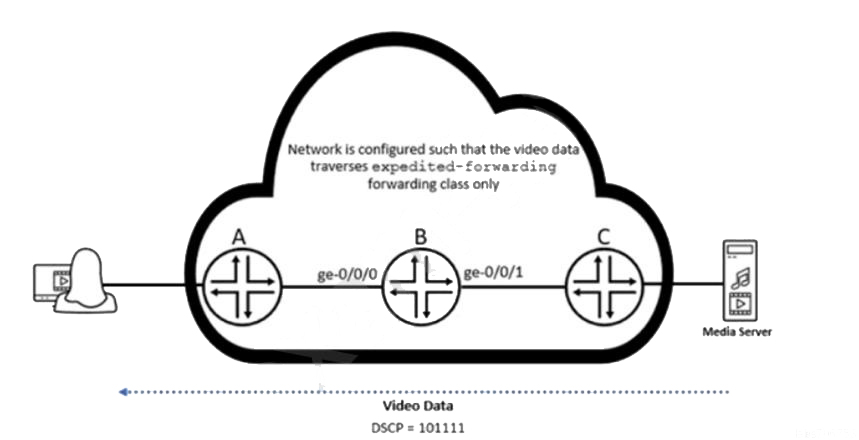
You enable the Multiple VLAN Registration Protocol (MVRP) to automate the creation and management of virtual LANs.
Which statement is correct in this scenario?
A Layer 2 connection does not expend across data centers. The IP subnet in a Layer 2 domain is confined within a single data center.
Which EVPN route type is used to communicate prefixes between the data centers?
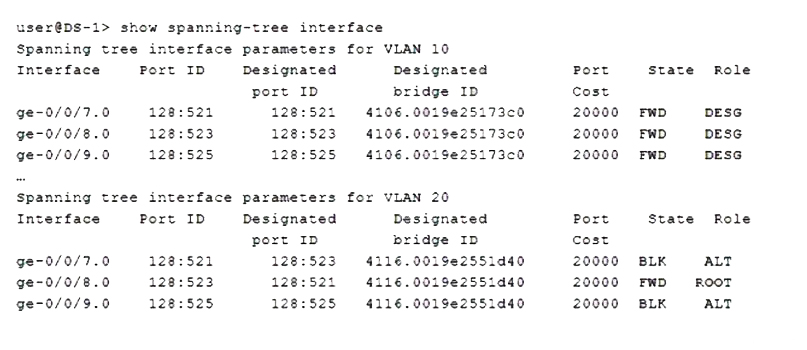
Referring to the exhibit, which two statements are correct? (Choose two.)
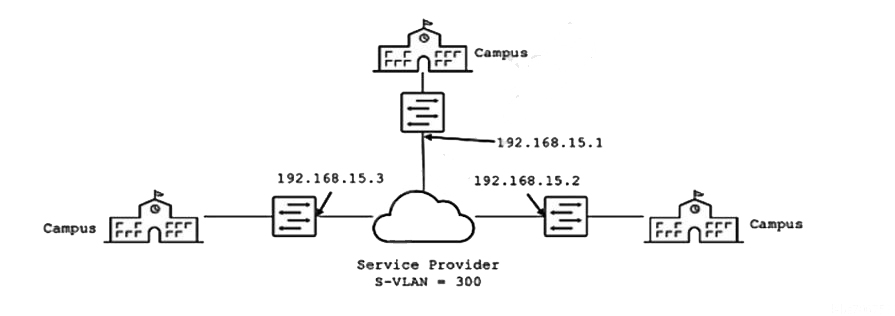
You want to provide Layer 2 connectivity between campus sites using Ethernet switches through a metro Ethernet service provider who is using Q-in-Q tagging on their network.
Referring to the exhibit, what are two design considerations in this environment? (Choose two.)
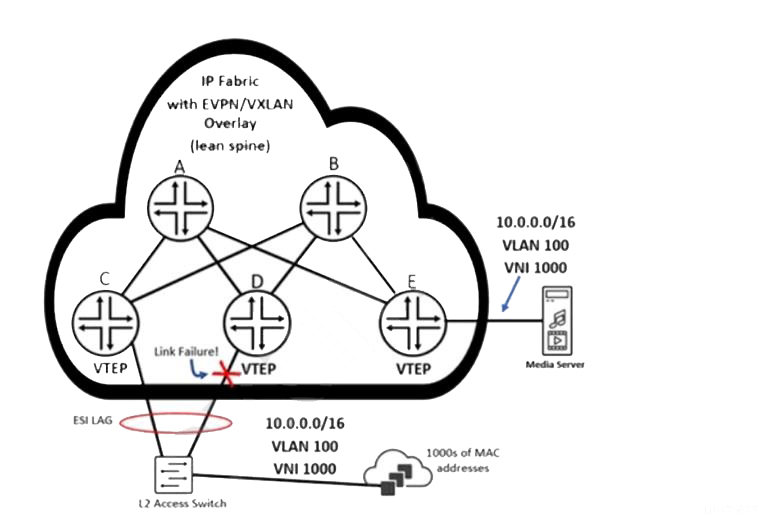
Referring to the exhibit, how will router E quickly learn that the remote MAC addresses are no longer reachable through the router attached to the failed link?
You are asked to enforce user authentication using a captive portal before users access the corporate network.
Which statement is correct in this scenario?
Your EX Series switch has IP telephones and computers connected to a single switch port. You are considering implementing the voice VLAN feature to help with this setup.
In this scenario, which two statements are correct? (Choose two.)
You are using 802.1X authentication in your network to secure all ports. You have a printer that does not support 802.1X and you must ensure that traffic is allowed to and from this printer without authentication.
In this scenario, what will satisfy the requirement?
Which two multicast listener registration protocols are supported in the Junos operating system? (Choose two.)



