MuleSoft MCD-Level-2 - MuleSoft Certified Developer - Level 2 (Mule 4)
Refer to the exhibit.
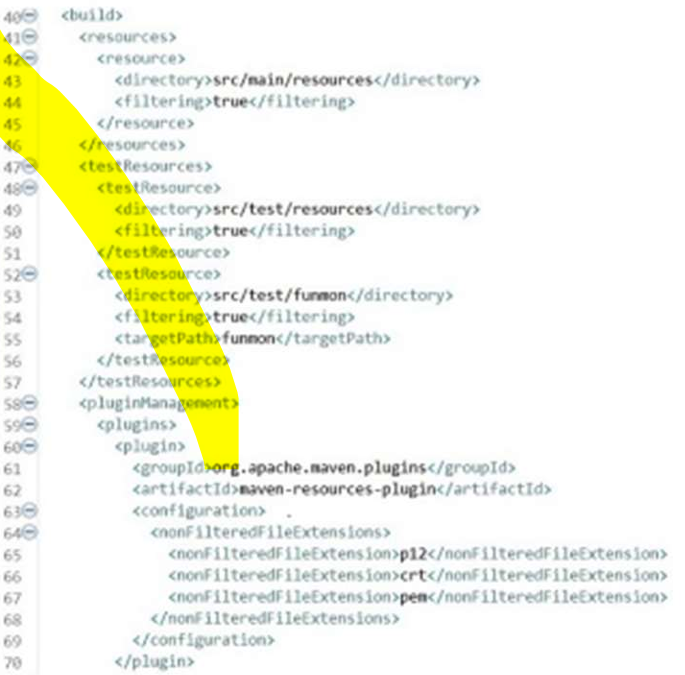
A Mule application pom.xml configures the Maven Resources plugin to exclude parsing binary files in the project’s src/main/resources/certs directory.
Which configuration of this plugin achieves a successful build?
A)
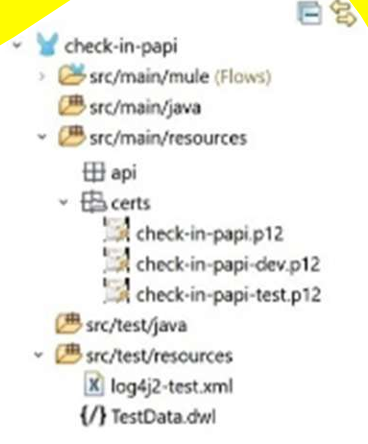
B)
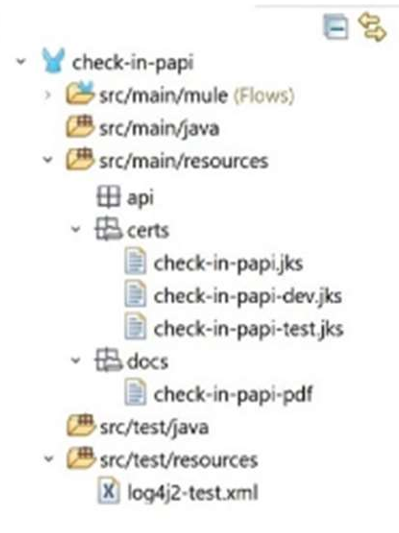
C)
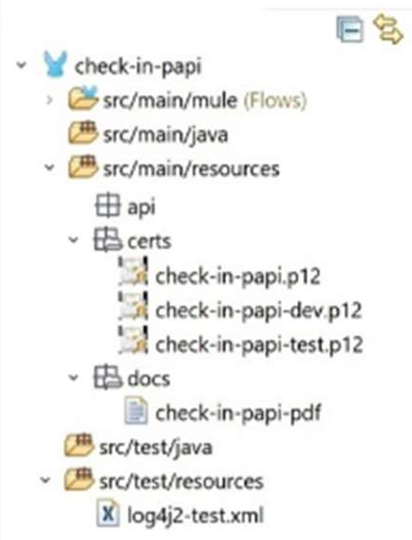
D)
Which type of cache invalidation does the Cache scope support without having to write any additional code?
Which statement is true about using mutual TLS to secure an application?
A Mule API receives a JSON payload and updates the target system with the payload. The developer uses JSON schemas to ensure the data is valid.
How can the data be validation before posting to the target system?
An order processing system is composed of multiple Mule application responsible for warehouse, sales and shipping. Each application communication using Anypoint MQ. Each message must be correlated against the original order ID for observability and tracing.
How should a developer propagate the order ID as the correlation ID across each message?
A healthcare portal needs to validate the token that it sends to a Mule API. The developer plans to implement a custom policy using the HTTP Policy Transform Extension to match the token received in the header from the heathcare portal.
Which files does the developer need to create in order to package the custom policy?
Which statement is true when working with correlation IDS?
When registering a client application with an existing API instance or API Group instance, what is required to manually approve or reject request access?



