Salesforce MuleSoft-Platform-Architect-I - Salesforce Certified MuleSoft Platform Architect (Mule-Arch-201)
Total 152 questions
In which layer of API-led connectivity, does the business logic orchestration reside?
A company deployed an API to a single worker/replica in the shared cloud in the U.S. West Region.
What happens when the Availability Zone experiences an outage?
What best explains the use of auto-discovery in API implementations?
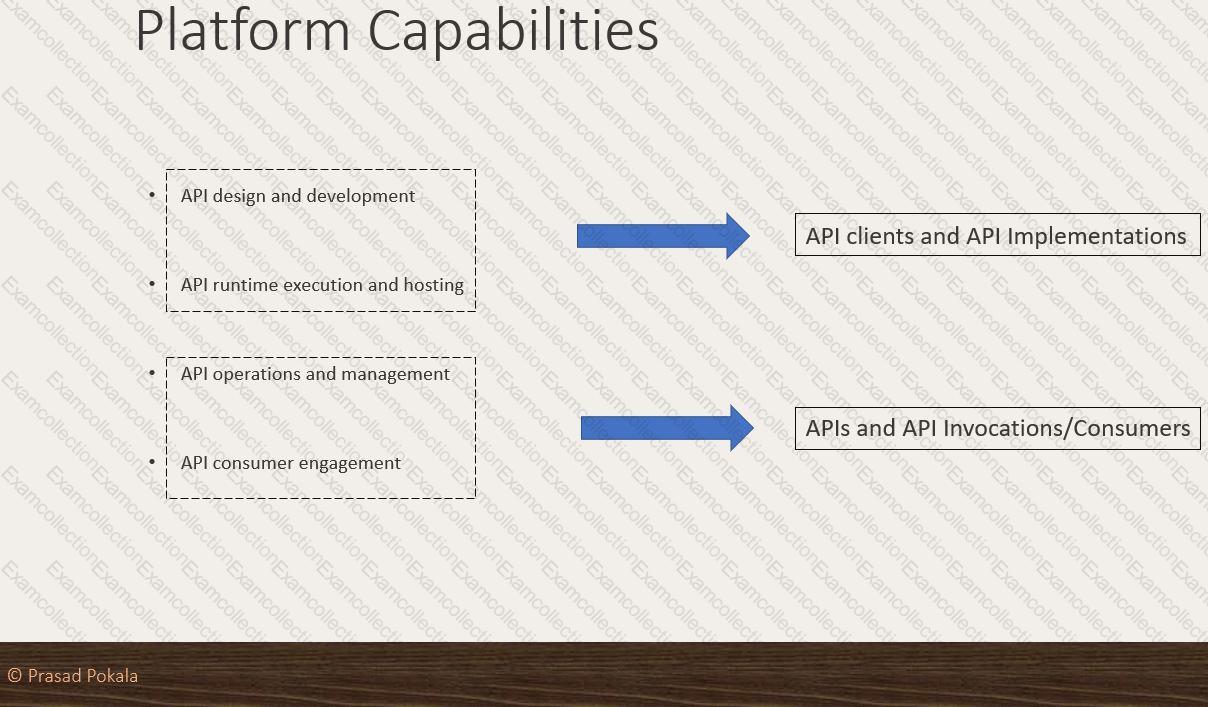
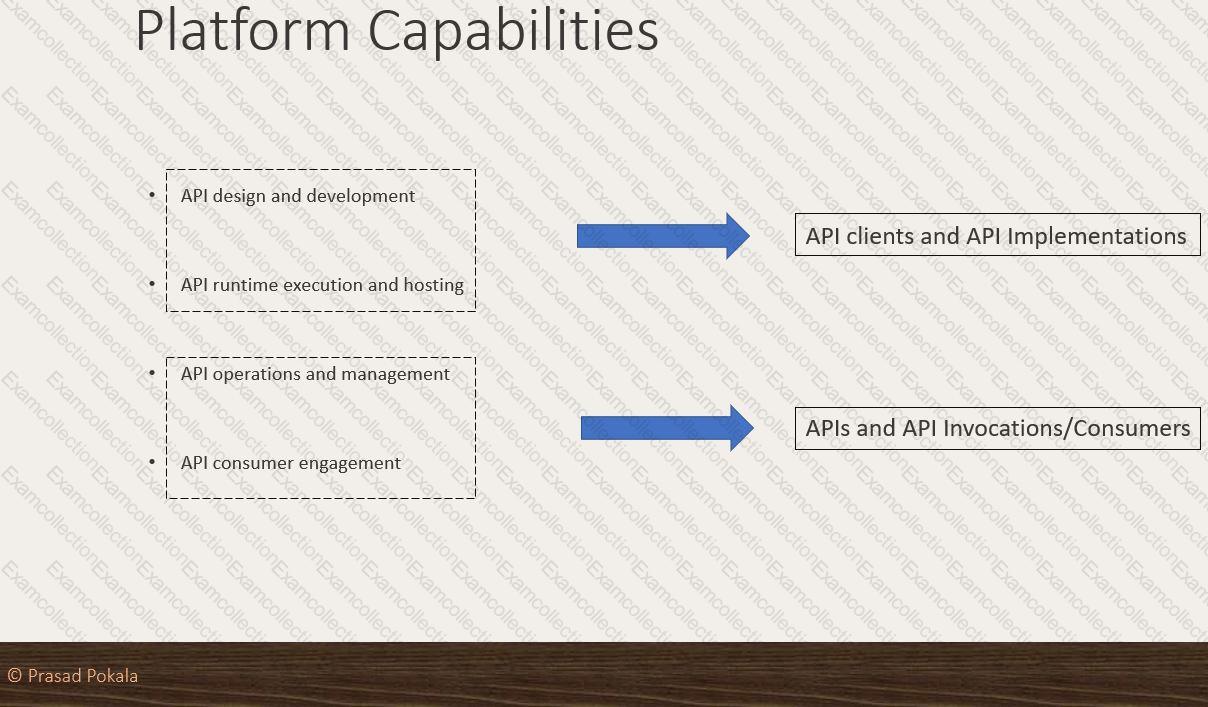
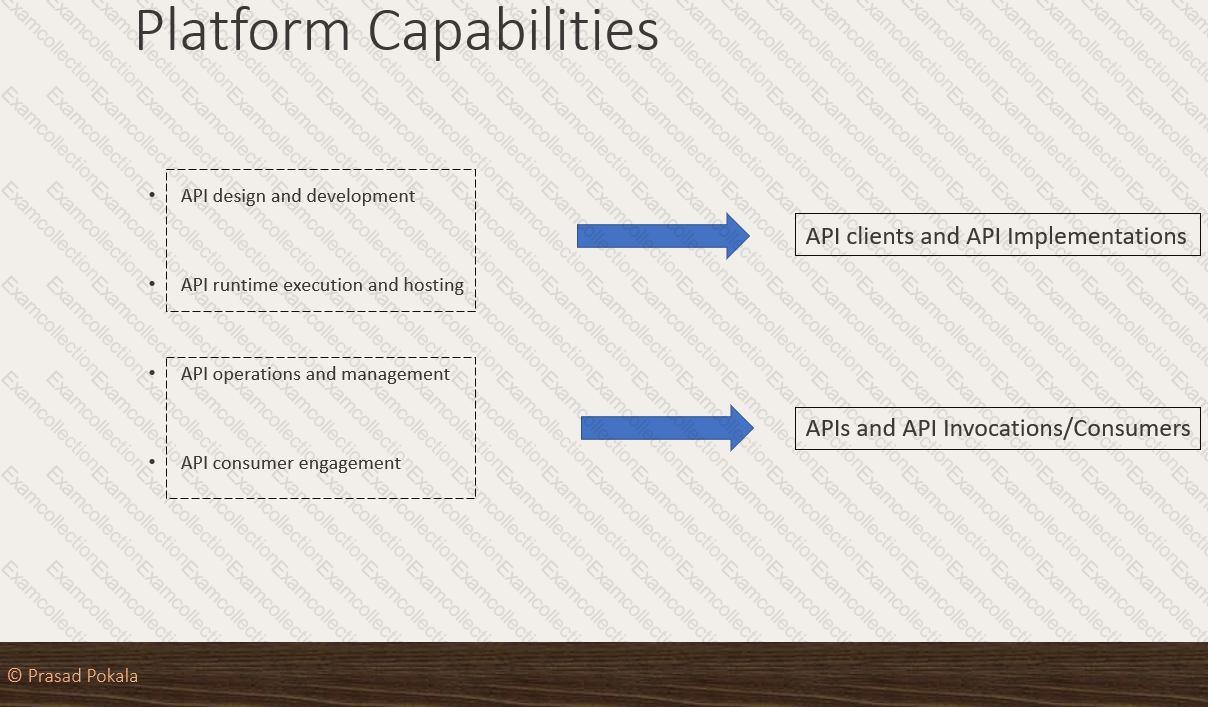
What are 4 important Platform Capabilities offered by Anypoint Platform?
What is most likely NOT a characteristic of an integration test for a REST API implementation?
What is a best practice when building System APIs?
What Anypoint Platform Capabilities listed below fall under APIs and API Invocations/Consumers category? Select TWO.
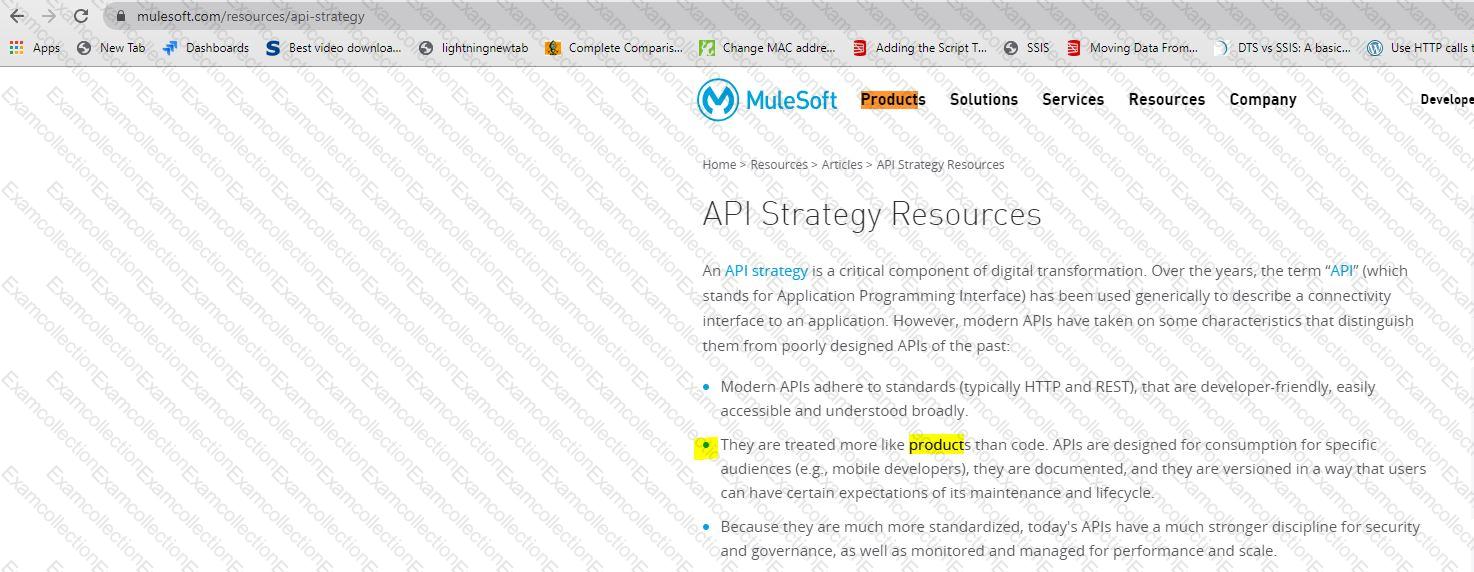
An organization makes a strategic decision to move towards an IT operating model that emphasizes consumption of reusable IT assets using modern APIs (as defined by MuleSoft).
What best describes each modern API in relation to this new IT operating model?
What correctly characterizes unit tests of Mule applications?
Which of the following best fits the definition of API-led connectivity?