Nutanix NCP-CN - Nutanix Certified Professional - Cloud Native (NCP-CN-6.10)
A Cloud Engineer manages an NKP environment and is preparing a machine image to become an NKP cluster node.
Which statement is regarding the default node preparation process?
A Platform Engineer will be deploying an NKP cluster in a dark site with no Internet access. The Cloud Administrator has provided a Linux VM for this purpose, so the engineer needs to prepare this VM to be used as a bastion host. Which two actions should the engineer take to complete this task? (Choose two.)
A Platform Engineer needs to create an NKP cluster on vSphere infrastructure, using the vSphere provisioning method. The cluster needs to have 3 worker node pools:
First node pool should consist of 6 worker nodes
Second node pool should consist of 3 worker nodes
Third node pool should consist of 3 worker nodesAdditionally, the worker nodes in the first node pool should be set to 10 CPUs, the second node pool workers should be set to 8 CPUs, and the third node pool workers should be set to 6 CPUs. What is the proper way to create the NKP cluster using the NKP CLI?
A Cloud Engineer is deploying an NKP management cluster and plans to deploy multiple NKP workload clusters from it. The management cluster will be on Nutanix infrastructure, but the NKP workload clusters may be deployed in multiple provisioning environments, such as:
Nutanix
AWS
AzureWhen the engineer deploys an NKP workload cluster in AWS, which two default behaviors will be performed by NKP on this newly-deployed cluster? (Choose two.)
A development Kubernetes cluster deployed with NKP is having performance issues. The Cloud Engineer commented that worker VMs are consuming a lot of CPU and RAM. The Platform Engineer took a look at the CPU and RAM statistics with Grafana and confirmed that the worker VMs are running out of CPU and memory. The Kubernetes cluster has 4 workers with 8 vCPUs and 32 GB RAM. What could the Platform Engineer do?
A company was using a test application called temp-shop developed in the temp-ecommerce NKP Starter cluster. Now, the cluster has just been taking up valuable resources that could be used for other projects, so the development team has decided to remove it.
Before proceeding, they verified that they had the cluster configuration file temp-ecommerce.conf.
What command should the development team execute to delete the cluster with its nodes and application?
Refer to the exhibits.
A Cloud Administrator had provisioned a Kubernetes cluster named demo that is no longer actively being used. A Quick review from the Systems Engineer confirms that the following VMs are part of the demo Kubernetes cluster
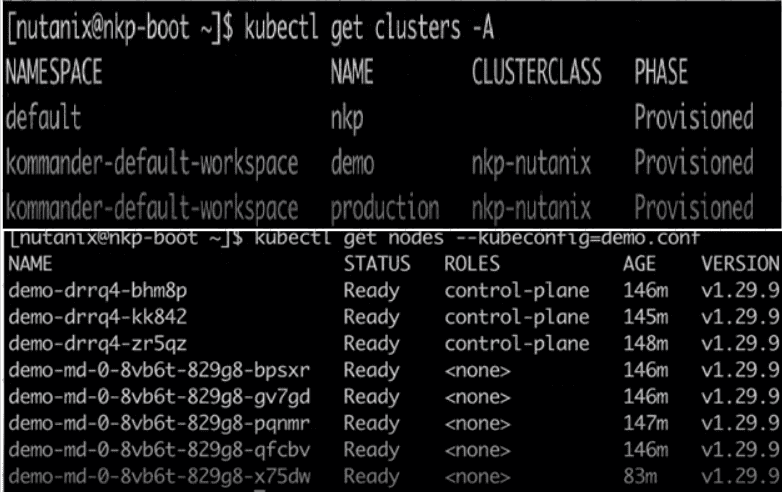
How should the demo cluster be properly deleted?
Which procedure should a Platform Engineer follow for setting up user authentication into an NKP cluster?
A development team has decided to implement an efficient logging system and use AWS S3 as storage to manage large volumes of logs in a scalable way.
The team followed these steps:
Set the WORKSPACE_NAMESPACE variable to the namespace copied in the previous step.
Created a config that overrode ConfigMap to update the storage configuration.
Updated the grafana-loki AppDeployment to apply the configuration override.However the implementation failed.What should the team do to be able to manage log storage in AWS?
Refer to Exhibit:
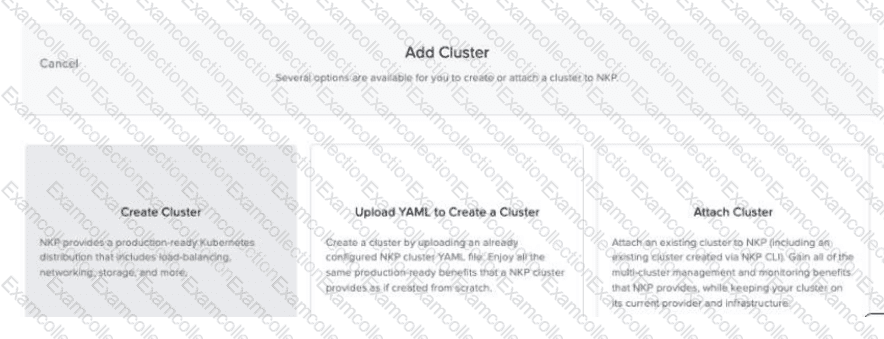
Using an NKP Ultimate license, a Platform Engineer has created a new workspace and needs to create a new Kubernetes cluster within this workspace. However, the engineer discovers that the Create Cluster option is grayed out, as shown in the exhibit. How should the engineer resolve this issue?



